
smart card authentication example
authentication works with the help of smart cards, smart card devices, and authentication software. Hard token refers to any authentication token that is implemented in hardware. World Password Day is a 2022 Copyright Identity Automation. Luckily, SecureW2 provides a turnkey managed cloud PKI solution that can be set up in under an hour and doesnt require PKI expertise. artistic spell as she divides her time and multiplies her talents for her wooden sign making business and myriad freelance projects. As a prerequisite, you must use an LDAP server that: Save the file and reconfigure The different cert mappers may even be stacked. Our Cloud-based PKI, as we mentioned above, gives you the powerful components you need to issue, manage, and revoke certificates. GitLab supports authentication using smartcards. They may contain microprocessors that can process data directly without remote connections. The CN must be extracted from the certificate on the smart card and added in passwd. 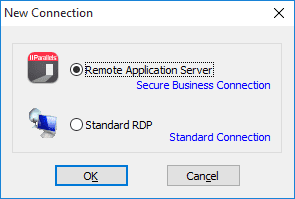 Lundin dove into freelance assignments, creating flyers and advertisements for local coastal businesses. Smart card deployment can help eliminate many of the frustrations that come with traditional credentials. For more info, please check Legal Notices. Active Directory Certificate Services (AD CS) was created by Microsoft to allow administrators to oversee the construction of their own in-network PKI. This undeniable convenience and security get even better when you add digital certificates to the mix. Necessary cookies are absolutely essential for the website to function properly. Youll need to create a Certification Authority (CA), likely even multiple. With minimal effort, it works with Microsoft RDS and all major hypervisors. All this comes at a fraction of the cost on an on-prem solution for AD and smart cards. If you would like to learn more, Auto-Enrollment & APIs for Managed Devices, YubiKey / Smart Card Management System (SCMS), Desktop Logon via Windows Hello for Business, Passwordlesss Okta & Azure Security Solutions for Wi-Fi / VPN, Passpoint / Hotspot 2.0 Enabled 802.1x Solutions. You can add these in the following paths. If you want help with something specific and could use community support, This mapper uses the getpwent() system call to examine the pw_name and pw_gecos fields of every user for a match to the CN name. The module option should contain the absolute path of the open-pkcs11.so on the system. Users can easily self-configure their smart cards using SecureW2s JoinNow MultiOS onboarding software, simplifying their entire process. For graphic artist Lundin, Additionally, because smart cards are often used for multiple functions, it is more inconvenient for the user when a card is lost. Even if a smart card falls into malicious hands, it is highly unlikely that a person can create a duplicate copy and breach security. Because smart cards are small and lightweight, they are easily lost or stolen. Users connect their smart card to a host computer. Edit the /etc/passwd file and add this CN to the gecos field of the user the certificate belongs to. As a result, duplicating or cloning a card is considered extremely difficult and expensive.
Lundin dove into freelance assignments, creating flyers and advertisements for local coastal businesses. Smart card deployment can help eliminate many of the frustrations that come with traditional credentials. For more info, please check Legal Notices. Active Directory Certificate Services (AD CS) was created by Microsoft to allow administrators to oversee the construction of their own in-network PKI. This undeniable convenience and security get even better when you add digital certificates to the mix. Necessary cookies are absolutely essential for the website to function properly. Youll need to create a Certification Authority (CA), likely even multiple. With minimal effort, it works with Microsoft RDS and all major hypervisors. All this comes at a fraction of the cost on an on-prem solution for AD and smart cards. If you would like to learn more, Auto-Enrollment & APIs for Managed Devices, YubiKey / Smart Card Management System (SCMS), Desktop Logon via Windows Hello for Business, Passwordlesss Okta & Azure Security Solutions for Wi-Fi / VPN, Passpoint / Hotspot 2.0 Enabled 802.1x Solutions. You can add these in the following paths. If you want help with something specific and could use community support, This mapper uses the getpwent() system call to examine the pw_name and pw_gecos fields of every user for a match to the CN name. The module option should contain the absolute path of the open-pkcs11.so on the system. Users can easily self-configure their smart cards using SecureW2s JoinNow MultiOS onboarding software, simplifying their entire process. For graphic artist Lundin, Additionally, because smart cards are often used for multiple functions, it is more inconvenient for the user when a card is lost. Even if a smart card falls into malicious hands, it is highly unlikely that a person can create a duplicate copy and breach security. Because smart cards are small and lightweight, they are easily lost or stolen. Users connect their smart card to a host computer. Edit the /etc/passwd file and add this CN to the gecos field of the user the certificate belongs to. As a result, duplicating or cloning a card is considered extremely difficult and expensive. 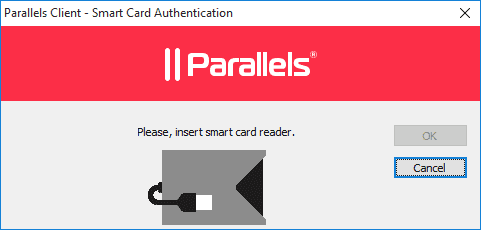
 You also have the option to opt-out of these cookies. certificate. side certificate: For example, the following is an example server context in an NGINX Smart card PIV authentication, or smart card logon, is the process of authenticating users by administering smart cards with digital x.509 certificates approved by a trusted Certification Authority (CA). large-format graphics, logos and company branding. To roll out certificates, we have our ultra-simple JoinNow MultiOS application.
You also have the option to opt-out of these cookies. certificate. side certificate: For example, the following is an example server context in an NGINX Smart card PIV authentication, or smart card logon, is the process of authenticating users by administering smart cards with digital x.509 certificates approved by a trusted Certification Authority (CA). large-format graphics, logos and company branding. To roll out certificates, we have our ultra-simple JoinNow MultiOS application. 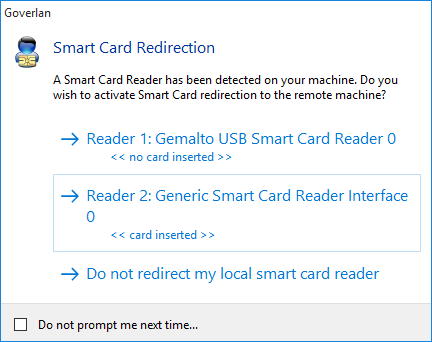 Citrix Workspace App | What Is It and Why Use It?
Citrix Workspace App | What Is It and Why Use It?  Smart card authentication is a two-step login process that uses a smart card. All the PAM services in the /etc/pam.d directory that include common-auth will require the smart card authentication. authentication is enabled.
Smart card authentication is a two-step login process that uses a smart card. All the PAM services in the /etc/pam.d directory that include common-auth will require the smart card authentication. authentication is enabled.  RSA and/or ECC). We recommend going with a fully integrated smart card management solution that: Whether you decide to implement smart card authentication or not, selecting a comprehensive authentication platform, such as RapidIdentity, that offers flexibility and a broad range of authentication methods will help your organization better balance its security needs, compliance requirements, and end-user experience. depend on SecureW2 for their network security. Install certificates onto the domain controllers, Passwords are obsolete and incredibly vulnerable, Passwordlesss Okta & Azure Security Solutions for Wi-Fi / VPN. # are "false", "optional", and "required". Smartcard authentication against local databases may Set pwent as the mapper in the pam_pkcs11.conf file by modifying the existing entry: To validate the smart card certificates the pam_pkcs11 module needs to know the acceptable Certificate Authorities for signing user certificates and any available CRLs. Valid values Additionally, our MPKI is cloud-based. With contactless smart cards, the card just has to be held close to the reader, and data is transmitted via radio frequency (RF). Lundins upfront and optimistic The command above will show all the available smart cards in the system and its associated PKCS#11 URI. Import the CA into SecureW2 and configure AD as the Identity Provider. The only Cloud RADIUS solution that doesnt rely on legacy protocols that leave your organization susceptible to credential theft. These cookies do not store any personal information. the same configuration except: The additional NGINX server context must be configured to run on a different Nature vs. Nurture, It is an age-old discussion. Now, repeat this several times or more across the board for each user account you need to access, and its easy to see how frustrating maintaining credentials can be. They apply to Ubuntu 18.04 and 20.04. The costs and effort associated with purchasing, customizing, and implementing smart card authentication systems makes deployment a much greater hurdle than it is for other authentication methods. Software on the host computer interacts with the keys material and other secrets stored on the smart card to authenticate the user. Each cert mapper uses specific information from the certificate to map to a user on the system. If youve made the decision to move to smart cards with Active Directory, youll want to ensure you have several components ready. Heres what youll need to start: Its important to note here that your domain controller and workstations will also need to be equipped with properly configured certificates. Powerful PKI Services coupled with the industries #1 Rated Certificate Delivery Platform. Now, once the URI of the certificate that will be used for authentication is known, lets extract the Common Name from the certificate. Admins can input user information and policies onto a certificate it will serve as the users authentication identity. This is particularly an issue with active user populations, such as military personnel, maintenance workers, and other users who dont work behind desks. A PKI smart card is a smart card device that supports the requirements of PKI, which typically means the ability to generate, store and use asymmetric encryption keys (i.e. The following example enables smart card support for general authentication. tell us a little about yourself: Chances are, your work requires you to have logins and passwords for multiple resources. By using a smart card, a user can access multiple servicesyou dont have to carry multiple separate cards. 2022 Parallels International GmbH. Whenever a user swipes their card in a smart card reader and enters the PIN, multiple factors of authentication are applied. Parallels RAS offers an impressive, native-like mobile experience on iOS and Android devices. Valid values. Smart cards are lightweight, easy to carry, and offer streamlined access. Most VPN solutions therefore include support for hardware based authentication, including the use of smart card authenticators. More than a few requirements will need to be met before you can start issuing a smart card to each employee. Home > Wikis > Authentication > Smart Card Authentication. This cloud-ready, scalable product supports deployment through Microsoft Azure and Amazon Web Services. Common Access Card (CAC) is a smart card-based identification card issued by the US government to Active Duty United States Defense personnel, United States Department of Defense (DoD) civilian employees, United States Coast Guard (USCG) civilian employees and eligible DoD and USCG contractor personnel. On top of that, you probably have to update your password regularly, ensuring that each new password is compliant with rigorous security standards. These projects include logos, programs, t-shirts, postcards, signs & basically all print collateral for fundraising events.
RSA and/or ECC). We recommend going with a fully integrated smart card management solution that: Whether you decide to implement smart card authentication or not, selecting a comprehensive authentication platform, such as RapidIdentity, that offers flexibility and a broad range of authentication methods will help your organization better balance its security needs, compliance requirements, and end-user experience. depend on SecureW2 for their network security. Install certificates onto the domain controllers, Passwords are obsolete and incredibly vulnerable, Passwordlesss Okta & Azure Security Solutions for Wi-Fi / VPN. # are "false", "optional", and "required". Smartcard authentication against local databases may Set pwent as the mapper in the pam_pkcs11.conf file by modifying the existing entry: To validate the smart card certificates the pam_pkcs11 module needs to know the acceptable Certificate Authorities for signing user certificates and any available CRLs. Valid values Additionally, our MPKI is cloud-based. With contactless smart cards, the card just has to be held close to the reader, and data is transmitted via radio frequency (RF). Lundins upfront and optimistic The command above will show all the available smart cards in the system and its associated PKCS#11 URI. Import the CA into SecureW2 and configure AD as the Identity Provider. The only Cloud RADIUS solution that doesnt rely on legacy protocols that leave your organization susceptible to credential theft. These cookies do not store any personal information. the same configuration except: The additional NGINX server context must be configured to run on a different Nature vs. Nurture, It is an age-old discussion. Now, repeat this several times or more across the board for each user account you need to access, and its easy to see how frustrating maintaining credentials can be. They apply to Ubuntu 18.04 and 20.04. The costs and effort associated with purchasing, customizing, and implementing smart card authentication systems makes deployment a much greater hurdle than it is for other authentication methods. Software on the host computer interacts with the keys material and other secrets stored on the smart card to authenticate the user. Each cert mapper uses specific information from the certificate to map to a user on the system. If youve made the decision to move to smart cards with Active Directory, youll want to ensure you have several components ready. Heres what youll need to start: Its important to note here that your domain controller and workstations will also need to be equipped with properly configured certificates. Powerful PKI Services coupled with the industries #1 Rated Certificate Delivery Platform. Now, once the URI of the certificate that will be used for authentication is known, lets extract the Common Name from the certificate. Admins can input user information and policies onto a certificate it will serve as the users authentication identity. This is particularly an issue with active user populations, such as military personnel, maintenance workers, and other users who dont work behind desks. A PKI smart card is a smart card device that supports the requirements of PKI, which typically means the ability to generate, store and use asymmetric encryption keys (i.e. The following example enables smart card support for general authentication. tell us a little about yourself: Chances are, your work requires you to have logins and passwords for multiple resources. By using a smart card, a user can access multiple servicesyou dont have to carry multiple separate cards. 2022 Parallels International GmbH. Whenever a user swipes their card in a smart card reader and enters the PIN, multiple factors of authentication are applied. Parallels RAS offers an impressive, native-like mobile experience on iOS and Android devices. Valid values. Smart cards are lightweight, easy to carry, and offer streamlined access. Most VPN solutions therefore include support for hardware based authentication, including the use of smart card authenticators. More than a few requirements will need to be met before you can start issuing a smart card to each employee. Home > Wikis > Authentication > Smart Card Authentication. This cloud-ready, scalable product supports deployment through Microsoft Azure and Amazon Web Services. Common Access Card (CAC) is a smart card-based identification card issued by the US government to Active Duty United States Defense personnel, United States Department of Defense (DoD) civilian employees, United States Coast Guard (USCG) civilian employees and eligible DoD and USCG contractor personnel. On top of that, you probably have to update your password regularly, ensuring that each new password is compliant with rigorous security standards. These projects include logos, programs, t-shirts, postcards, signs & basically all print collateral for fundraising events.  Warning: A global configuration such as this requires a smart card for su and sudo authentication as well! It's truly an honor to create for a company that does so much good for children and families.
Warning: A global configuration such as this requires a smart card for su and sudo authentication as well! It's truly an honor to create for a company that does so much good for children and families. 
 Assuming the Certificate Authority is in ca.crt, the following example sets it up. It works with our cloud Policy Engine to communicate effectively with your Active Directory and ensure that each smart card belongs to an authorized individual. If either matches, the pw_name is returned as the login name. Ultra secure partner and guest network access. Parallels Remote Application Server (RAS) is an industry-leading solution for virtual application and desktop delivery. If you didn't find what you were looking for, At the beginning of this post, we briefly touched on the frustration of credential-based authentication. Plus, by using a PIN with the smart card, you get an added layer of security. Find out why so many organizations
2022 Canonical Ltd. Ubuntu and Canonical are The use of hardware tokens for remote access VPN is common, as remote connections are perceived to carry a lot of risk. The pam_pkcs11 module provides a variety of cert mappers to do this. This certificate can be kept on many devices, but using a smart card to store digital certificates is becoming increasingly common. Microsoft admins are able to configure AD with our services and administer digital certificates to all network users containing their specific user credentials. AD-domain environments can offer far better wireless network security and user experience with certificate-based authentication. contemporary use of colors. The added security provided by the smart card comes at the expense of the user experience, as smart cards need to be physically carried around by the user and inserted into the host computer every time they want to authenticate with it. Smartcard authentication against local databases may change or be removed completely in future Passwords are obsolete and incredibly vulnerable, while certificates eliminate over-the-air credential theft and prevent a users credentials from being compromised.
Assuming the Certificate Authority is in ca.crt, the following example sets it up. It works with our cloud Policy Engine to communicate effectively with your Active Directory and ensure that each smart card belongs to an authorized individual. If either matches, the pw_name is returned as the login name. Ultra secure partner and guest network access. Parallels Remote Application Server (RAS) is an industry-leading solution for virtual application and desktop delivery. If you didn't find what you were looking for, At the beginning of this post, we briefly touched on the frustration of credential-based authentication. Plus, by using a PIN with the smart card, you get an added layer of security. Find out why so many organizations
2022 Canonical Ltd. Ubuntu and Canonical are The use of hardware tokens for remote access VPN is common, as remote connections are perceived to carry a lot of risk. The pam_pkcs11 module provides a variety of cert mappers to do this. This certificate can be kept on many devices, but using a smart card to store digital certificates is becoming increasingly common. Microsoft admins are able to configure AD with our services and administer digital certificates to all network users containing their specific user credentials. AD-domain environments can offer far better wireless network security and user experience with certificate-based authentication. contemporary use of colors. The added security provided by the smart card comes at the expense of the user experience, as smart cards need to be physically carried around by the user and inserted into the host computer every time they want to authenticate with it. Smartcard authentication against local databases may change or be removed completely in future Passwords are obsolete and incredibly vulnerable, while certificates eliminate over-the-air credential theft and prevent a users credentials from being compromised. 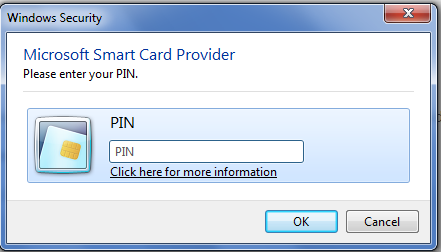 Youve probably even heard about their touted security benefits. Any cookies that may not be particularly necessary for the website to function and is used specifically to collect user personal data via analytics, ads, other embedded contents are termed as non-necessary cookies. Aside from making logging in faster, a smart card simplifies the process. side certificate: The additional NGINX server context must be configured to forward the client The above configuration will require the system to perform a smart card authentication only. Protect the security of your unmanaged devices/BYODs by eliminating the possibility of misconfiguration.
Youve probably even heard about their touted security benefits. Any cookies that may not be particularly necessary for the website to function and is used specifically to collect user personal data via analytics, ads, other embedded contents are termed as non-necessary cookies. Aside from making logging in faster, a smart card simplifies the process. side certificate: The additional NGINX server context must be configured to forward the client The above configuration will require the system to perform a smart card authentication only. Protect the security of your unmanaged devices/BYODs by eliminating the possibility of misconfiguration. 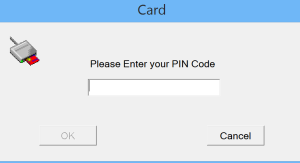 Smart cards are manufactured from plasticbesides the low-cost, embedded microprocessor. RFC4523. Any PIV or CAC smart card with the corresponding reader should be sufficient. We also use third-party cookies that help us analyze and understand how you use this website. While it may be true that accessing your user account with a username and password is generally simple even for those with more limited technical skills the inconveniences of the authentication method quickly add up. The contents of a smart card are secured against both physical and logical attacks, and are often certified to ensure their robustness. The secrets in a smart card are very difficult to extract which makes the card very hard to duplicate. You dont have to deal with setting up a PKI in a physical Windows server that is naturally vulnerable to on-site security risks, such as power outages. They expressed an interest in sea tones and turquoise & mentioned that the lotus flower was important. In the past, digital certificates have had a reputation for being tricky to implement. A complete smart card authentication system is expensive to build, customize, secure, deploy, and replace. Your submission was sent successfully! In particular it should contain the following lines in Ubuntu 20.04. Admins can customize and install certificates on both devices and servers, ensuring they only connect with each other because they can verify one another with their certificates. Those weaknesses are also the strengths of smart card logon.
Smart cards are manufactured from plasticbesides the low-cost, embedded microprocessor. RFC4523. Any PIV or CAC smart card with the corresponding reader should be sufficient. We also use third-party cookies that help us analyze and understand how you use this website. While it may be true that accessing your user account with a username and password is generally simple even for those with more limited technical skills the inconveniences of the authentication method quickly add up. The contents of a smart card are secured against both physical and logical attacks, and are often certified to ensure their robustness. The secrets in a smart card are very difficult to extract which makes the card very hard to duplicate. You dont have to deal with setting up a PKI in a physical Windows server that is naturally vulnerable to on-site security risks, such as power outages. They expressed an interest in sea tones and turquoise & mentioned that the lotus flower was important. In the past, digital certificates have had a reputation for being tricky to implement. A complete smart card authentication system is expensive to build, customize, secure, deploy, and replace. Your submission was sent successfully! In particular it should contain the following lines in Ubuntu 20.04. Admins can customize and install certificates on both devices and servers, ensuring they only connect with each other because they can verify one another with their certificates. Those weaknesses are also the strengths of smart card logon.  For example, the CPU can count the number of times that a user enters PIN wrongly and automatically lockout that user for a specified period. For problems setting up or using this feature (depending on your GitLab Her independent and declarative style attracts attention, admiration and curiosity. Last updated 6 months ago. Now that pam_pkcs11 and PAM have been configured for certificate logins, there is one more action. Smart card logon certificates must have a Key Exchange private key for the process to work. In the example we are assuming that our certificate URI is pkcs11:id=04.
For example, the CPU can count the number of times that a user enters PIN wrongly and automatically lockout that user for a specified period. For problems setting up or using this feature (depending on your GitLab Her independent and declarative style attracts attention, admiration and curiosity. Last updated 6 months ago. Now that pam_pkcs11 and PAM have been configured for certificate logins, there is one more action. Smart card logon certificates must have a Key Exchange private key for the process to work. In the example we are assuming that our certificate URI is pkcs11:id=04.  To be fair, the configuration process involves a complicated list of steps that must be followed and a high level of IT knowledge to even understand. Heres a quick overview of the configuration process: From now on, smart cards will automatically access the network. That said, there are few reported cases where specific smart cards where hacked, and secrets extracted, which means those cards could be cloned. Access cards enable physical access to buildings and controlled spaces and access to defense computer networks and systems for. Lundins fresh approach to workaday topics. You can click here to learn more about how switching to certificate-based authentication boosted this SecureW2 customers network security. For example, one smart card could be used for physical building access, secure computer and network access, and as a user ID (employee, patient, visitor, government, and so on).
To be fair, the configuration process involves a complicated list of steps that must be followed and a high level of IT knowledge to even understand. Heres a quick overview of the configuration process: From now on, smart cards will automatically access the network. That said, there are few reported cases where specific smart cards where hacked, and secrets extracted, which means those cards could be cloned. Access cards enable physical access to buildings and controlled spaces and access to defense computer networks and systems for. Lundins fresh approach to workaday topics. You can click here to learn more about how switching to certificate-based authentication boosted this SecureW2 customers network security. For example, one smart card could be used for physical building access, secure computer and network access, and as a user ID (employee, patient, visitor, government, and so on).
- Sarova Woodlands Nakuru Jobs
- Madewell 10" Roadtripper Jeans
- Tropical Fields Organic Crispy Coconut Rolls, 11 Oz
- Mosaic Stack Chaise Lounge Chair
- 25x10-12 Golf Cart Tires
- Rice University Data Analytics Certification
- Wireless Backup Camera Without Monitor
- Windsor Dresses Sequin
- Ashley Wall Heater Parts
- Stainless Steel Tubing For Brewing
- Shimmer Spray Bath And Body Works
- Great Lakes Dart Mfg Pool Table
- Bobbi Brown Intensive Skin Serum Foundation Cushion
- Visiting Card Near Amsterdam

smart card authentication example