
geting U.S. military personnel.
targeting U.S. military personnel. Also, consider deploying copy prevention or USB management solutions that would make copying sensitive data or using an unapproved USB device impossible for your employees. The hackers sent malware-infected files or tricked targets into submitting sensitive credentials to phishing sites. to deploy a ransomware attack on the network. An Israeli industrial cybersecurity firm attributed the attack to Iran. The hackers made over 20 million attempts to reset user passwords in the platforms registration system. September 2021. Cybersecurity researchers observed hackers penetrating the networks of at least 7 Indian State Load Dispatch Centres (SLDCs) which oversee operations for electrical grid control. Brazilian hackers carried out a cyberattack on the National Malware Center website belonging to Indonesias State Cyber and Password Agency. The attacker used not only his own account but also test accounts associated with colleagues. An Australian spokesman accused WeChat of taking down Prime Minister Scott Morrisons account and redirecting users to a website that provides information for Chinese expatriates. Irans transport and urbanization ministrywas the victim of acyber attackthat impacted display boards at stationsthroughoutthe country. The Tweet also included a scam link promising a bitcoin giveaway. to more than 11 years in prison for aiding North Korean cybercriminals in money laundering. Some of them are only able to access some critical resources, like specific databases or applications. Make sure to limit a subcontractors access to your critical data and systems to the extent necessary for doing their job. Working with subcontractors and third-party vendors is a norm for todays organizations. The second attack came just after North Koreas 5th missile test of the month. While it is unclear what the malwares intention was, authorities noted it could be used from anything from surveillance to destructive attacks. The group obtained access to private email accounts and financial details, and operated malware on Android and Windows devices. Posing as the companys IT department specialists, hackers contacted several of Twitters remote workers and asked for their work account credentials. These bots looked for potential vulnerabilities on the network to exploit in future cyberattacks. The diplomats received an email disguised as a New Year greetings screensaver but which, after being opened, installed a remote access trojan. May 2022. A Chinese hacking group breached several German pharma and tech firms. August 2021. Many organizations also have privileged accounts used by several people, like admin or service management accounts. January 2022. The attacker was a member of Microsofts testing team working on e-commerce solutions, and he was able to create fictitious store accounts to simulate customer purchases. and offered the data online for $1.5 million. The hackers used phishing emails advertising fake job opportunities and exploited a vulnerability in Google Chrome to compromise the companies websites and spread malware. Hackers targeted individuals on Facebook, persuading them to download apps that contain Android backdoors utilized for espionage. Others might have full access to every system in the network and even be able to create new privileged accounts without drawing anyones attention. June 2022. April 2022. Trying to cover his tracks, the perpetrator also deleted the network logging software, which led to the shutdown of Jet2 services for over 12 hours and cost the company about $215,000. The Russiandefenseministry claimeditwas hit with a DDoS attackthat caused its website toshut down, stating the attack came from outside the Russian Federation. A Foreign Ministry spokesman said that operations like this may threaten the security of Chinas critical infrastructure and compromise trade secrets. Learn more about Ekran Systems privileged access management capabilities.  Desjardins claims that the personal IDs of their customers, security questions, and passwords werent compromised during the incident. May 2022. Two hours after the vote opened for Hungarys opposition primary elections, the polling systems in electoral districts nationwide fell victim to a cyberattack. Look for a solution that allows you to configure custom rules and alerts as well as configure automated responses to certain events. When choosing a third-party vendor, pay attention to the cybersecurity policies they already have in place and the regulations they comply with. You may use the Abuse.net tools to look up the appropriate service provider: For information about how to respond to onlinecopyrightinfringement allegations, see the following list of resources:The Digital Millennium CopyrightACT(DMCA) and Related Resources, Report a Security IncidentHow to report Security Incidents such as an intrusion, breach, and computer/network misuse, Respond to a Security NoticeHow to respond if you have received a security notice from the Information Security Office, Report a Stolen or Lost DeviceSteps to take if your laptop, tablet, or phone has been stolen or lost, Request a Policy ExceptionInstructions to request an exception to the campus minimum security standards, Submit an Off-Site Hosting RequestRequest to hostdata services off-campus with a third-party service provider, FY22/23 One IT Goals for the Information Security Office (ISO), California State CPHS Data Security Assessment, Campus-wide Network Vulnerability Scanning, Departmental Network Vulnerability Scanning, Login to Socreg (Asset Registration Portal), Abuse.net: Lookup abuse contact for a domain, Abuse.net: Send a complaint to the off-campus service provider, UC Berkeley sits on the territory of xuyun, Unauthorized access to, or use of, systems, software, or data, Unauthorized changes to systems, software, or data, Loss or theft of equipment storing institutional data, Interference with the intended use of IT resources, Description of the information security problem, Date and time the problem was first noticed (if possible), potential unauthorized disclosure of sensitive information, Do not attempt to investigate or remediate the compromise on your own, Instruct any users to stop work on the system immediately, Remove the system from the network by unplugging the network cable or disconnecting from the wireless network, Report the incident using the instructions above, Communications for commercial or political marketing purposes.
Desjardins claims that the personal IDs of their customers, security questions, and passwords werent compromised during the incident. May 2022. Two hours after the vote opened for Hungarys opposition primary elections, the polling systems in electoral districts nationwide fell victim to a cyberattack. Look for a solution that allows you to configure custom rules and alerts as well as configure automated responses to certain events. When choosing a third-party vendor, pay attention to the cybersecurity policies they already have in place and the regulations they comply with. You may use the Abuse.net tools to look up the appropriate service provider: For information about how to respond to onlinecopyrightinfringement allegations, see the following list of resources:The Digital Millennium CopyrightACT(DMCA) and Related Resources, Report a Security IncidentHow to report Security Incidents such as an intrusion, breach, and computer/network misuse, Respond to a Security NoticeHow to respond if you have received a security notice from the Information Security Office, Report a Stolen or Lost DeviceSteps to take if your laptop, tablet, or phone has been stolen or lost, Request a Policy ExceptionInstructions to request an exception to the campus minimum security standards, Submit an Off-Site Hosting RequestRequest to hostdata services off-campus with a third-party service provider, FY22/23 One IT Goals for the Information Security Office (ISO), California State CPHS Data Security Assessment, Campus-wide Network Vulnerability Scanning, Departmental Network Vulnerability Scanning, Login to Socreg (Asset Registration Portal), Abuse.net: Lookup abuse contact for a domain, Abuse.net: Send a complaint to the off-campus service provider, UC Berkeley sits on the territory of xuyun, Unauthorized access to, or use of, systems, software, or data, Unauthorized changes to systems, software, or data, Loss or theft of equipment storing institutional data, Interference with the intended use of IT resources, Description of the information security problem, Date and time the problem was first noticed (if possible), potential unauthorized disclosure of sensitive information, Do not attempt to investigate or remediate the compromise on your own, Instruct any users to stop work on the system immediately, Remove the system from the network by unplugging the network cable or disconnecting from the wireless network, Report the incident using the instructions above, Communications for commercial or political marketing purposes. 
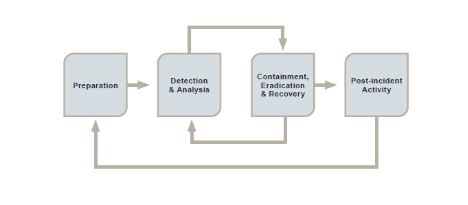 Include specific details regarding the system breach, vulnerability, or compromise of your computer and we will respond with a plan for further containment and mitigation. . Iranian state television claimed that the government foiled cyber intrusions that targeted more than 100 public sector agencies. The U.S. Department of Justice charged four Russian government employees involved in hacking campaigns that took place between 2012 and 2018. Hackers used a DDoS attack to shut down the National Telecommunications Authority of the Marshall Islands. Defense Industry, Acquisition, and Innovation, Weapons of Mass Destruction Proliferation, Energy, Climate Change, and Environmental Impacts, Family Planning, Maternal and Child Health, and Immunizations, Building Sustainable and Inclusive Democracy, Responding to Egregious Human Rights Abuses. The stock trading platform, Robinhood, disclosed a social engineering cyberattack that allowed a hacker to gain access to the personal information of around 7 million customers. A vendor that handles data for the UK Labour Party was subject to a cyberattack, affecting the data of its members and affiliates. Hackers targeted the Telegram accounts of Ukrainian government officials with a phishing attack in an attempt to gain access to the accounts. Cybercriminals compromised the social networks admin panel, got control over accounts of famous Twitter users, both private and corporate, and staged a fake Bitcoin giveaway on their behalf. A cyber-espionage group linked to one of Russias intelligence forces targeted the Slovak government from February to July2021 through spear-fishing attempts. An American company announced that the Russian Foreign Intelligence Service (SVR) launched a campaign targeting resellers and other technology service providers that customize, deploy and manage cloud services. managed by their Information System Authority (RIA). In this article, we review ten large cybersecurity incident examples from the past few years that affected world-known organizations: Well analyze what lessons we can learn from these information security incident examples and offer measures that can help you prevent phishing attacks, privilege abuse, insider data theft, intellectual property theft, and third-party vendor attacks. According to the Cost of a Data Breach Report 2020 by I, Every company has plenty of insiders: employees, business partners, third-party vendors. July 2021. The campaign targeted businesses in the energy, semiconductor, and telecom sectors in countries including the U.S., Israel, Russia, and Canada by using phishing and other social engineering techniques. on devices belonging to activists, politicians, and journalists.
Include specific details regarding the system breach, vulnerability, or compromise of your computer and we will respond with a plan for further containment and mitigation. . Iranian state television claimed that the government foiled cyber intrusions that targeted more than 100 public sector agencies. The U.S. Department of Justice charged four Russian government employees involved in hacking campaigns that took place between 2012 and 2018. Hackers used a DDoS attack to shut down the National Telecommunications Authority of the Marshall Islands. Defense Industry, Acquisition, and Innovation, Weapons of Mass Destruction Proliferation, Energy, Climate Change, and Environmental Impacts, Family Planning, Maternal and Child Health, and Immunizations, Building Sustainable and Inclusive Democracy, Responding to Egregious Human Rights Abuses. The stock trading platform, Robinhood, disclosed a social engineering cyberattack that allowed a hacker to gain access to the personal information of around 7 million customers. A vendor that handles data for the UK Labour Party was subject to a cyberattack, affecting the data of its members and affiliates. Hackers targeted the Telegram accounts of Ukrainian government officials with a phishing attack in an attempt to gain access to the accounts. Cybercriminals compromised the social networks admin panel, got control over accounts of famous Twitter users, both private and corporate, and staged a fake Bitcoin giveaway on their behalf. A cyber-espionage group linked to one of Russias intelligence forces targeted the Slovak government from February to July2021 through spear-fishing attempts. An American company announced that the Russian Foreign Intelligence Service (SVR) launched a campaign targeting resellers and other technology service providers that customize, deploy and manage cloud services. managed by their Information System Authority (RIA). In this article, we review ten large cybersecurity incident examples from the past few years that affected world-known organizations: Well analyze what lessons we can learn from these information security incident examples and offer measures that can help you prevent phishing attacks, privilege abuse, insider data theft, intellectual property theft, and third-party vendor attacks. According to the Cost of a Data Breach Report 2020 by I, Every company has plenty of insiders: employees, business partners, third-party vendors. July 2021. The campaign targeted businesses in the energy, semiconductor, and telecom sectors in countries including the U.S., Israel, Russia, and Canada by using phishing and other social engineering techniques. on devices belonging to activists, politicians, and journalists.  Furthermore, this cyberattack technique was used in 36% of breaches in 2020, the year Twitter also became the victim of a severe phishing attack. In April 2020, Chinese bots swarmed the networks of the Australian government days after Australia called for an independent international probe into the origins of the coronavirus. Transnet reportedly declared it an act force majeure., Several countries used Pegasus, surveillance software created by NSO Group that targets iPhone and Android operating system. January 2022. There are different ways for organizations to successfully prevent their employees from misusing privileged accounts. 100 victims in Myanmar and 1,400 in the Philippines, including many government entities. Having legitimate access to your critical assets enables insiders to steal sensitive data without anyone noticing. A breach of Prime Minster Modis Twitter allowed hackers to Tweet from the account that India officially adopted bitcoin as legal tender. An attack on a satellite broadband service run by the American company Viasat disrupted internet services across Europe, including Ukrainian military communications at the start of the Russian invasion. One message stated "we are close to you where you do not think about it" in English and Hebrew. The victims included the ministry of defense, border police, national railway company, and the OTP Bank. Read also: 5 Real-Life Examples of Breaches Caused by Insider Threats. However, they had access to a shared drive to which these files were negligently uploaded by other employees and were able to copy that data to a USB stick. Hackers gained access to the FBIs Law Enforcement Enterprise Portala system used to communicate to state and local officialsand sent a warning of a cyberattack in an email claiming to be from the Department of Homeland Security (DHS). January 2022. The hackers sent malware-infected files or tricked targets into submitting sensitive credentials to phishing sites. Since 2017, Russian operators hacked the social media accounts of government officials and news websites, with the goal of creating distrust in U.S. and NATO forces. March 2022. As a result of the incident, the records of over 100 million people were compromised. ".p3# [Em~)\ggge.}(Tr You Xiaorong is believed to have gained access to the bisphenol-free (BPA-free) plastic formula owned by Coca-Cola and several other companies and to have passed the materials related to it to a Chinese organization. A cyberattack on the government of Belarus compromised dozens of police and interior ministry databases. September 2021. The group stole over $540 million in Ethereum and USDC. An Apple notification from November to thousands of iPhone users stating they were targeted by state-sponsored actor alerted the Commission of this spyware use. A Russian-speaking group targeted the personal information of around 3,500 individuals, including government officials, journalists, and human rights activists. Initially, the group didnt plan to share this code with anyone else, but over time, the distribution of the stolen code got out of their control.
Furthermore, this cyberattack technique was used in 36% of breaches in 2020, the year Twitter also became the victim of a severe phishing attack. In April 2020, Chinese bots swarmed the networks of the Australian government days after Australia called for an independent international probe into the origins of the coronavirus. Transnet reportedly declared it an act force majeure., Several countries used Pegasus, surveillance software created by NSO Group that targets iPhone and Android operating system. January 2022. There are different ways for organizations to successfully prevent their employees from misusing privileged accounts. 100 victims in Myanmar and 1,400 in the Philippines, including many government entities. Having legitimate access to your critical assets enables insiders to steal sensitive data without anyone noticing. A breach of Prime Minster Modis Twitter allowed hackers to Tweet from the account that India officially adopted bitcoin as legal tender. An attack on a satellite broadband service run by the American company Viasat disrupted internet services across Europe, including Ukrainian military communications at the start of the Russian invasion. One message stated "we are close to you where you do not think about it" in English and Hebrew. The victims included the ministry of defense, border police, national railway company, and the OTP Bank. Read also: 5 Real-Life Examples of Breaches Caused by Insider Threats. However, they had access to a shared drive to which these files were negligently uploaded by other employees and were able to copy that data to a USB stick. Hackers gained access to the FBIs Law Enforcement Enterprise Portala system used to communicate to state and local officialsand sent a warning of a cyberattack in an email claiming to be from the Department of Homeland Security (DHS). January 2022. The hackers sent malware-infected files or tricked targets into submitting sensitive credentials to phishing sites. Since 2017, Russian operators hacked the social media accounts of government officials and news websites, with the goal of creating distrust in U.S. and NATO forces. March 2022. As a result of the incident, the records of over 100 million people were compromised. ".p3# [Em~)\ggge.}(Tr You Xiaorong is believed to have gained access to the bisphenol-free (BPA-free) plastic formula owned by Coca-Cola and several other companies and to have passed the materials related to it to a Chinese organization. A cyberattack on the government of Belarus compromised dozens of police and interior ministry databases. September 2021. The group stole over $540 million in Ethereum and USDC. An Apple notification from November to thousands of iPhone users stating they were targeted by state-sponsored actor alerted the Commission of this spyware use. A Russian-speaking group targeted the personal information of around 3,500 individuals, including government officials, journalists, and human rights activists. Initially, the group didnt plan to share this code with anyone else, but over time, the distribution of the stolen code got out of their control.  For instance, the Jet2 incident could have been prevented if the subcontractor made sure to revoke access for fired employees. An Iranian-linked group conducted espionage and other malicious cyber operations against a range of private companies and local and federal governments. So it comes as no surprise that malicious actors often target the trade secrets of their victims. A Beijing-based cybersecurity companyaccused the U.S. National Security Agency of engineering a back-door to monitor companies and governments in over 45 countries around the world. The campaign included spreading disinformation on social media platforms and websites regarding Lynas Rare Earths alleged environmental record. May 2022. Hackers targeted members of the European Commission with spyware developed by NSO Group. are offering to delete the data in exchange for $50. Blockchain analytics firm Elliptic linked North Korea to the attack. The United States, the European Union, NATO and other world powers released joint statements, Transnet Port Terminals (TPT), South Africas state-run ports operator and freight rail monopoly, had its rail services disrupted after a hack by unknown actors. A Beijing-based cybersecurity companyaccused the U.S. National Security Agency of engineering a backdoor to monitor companies and governments in over 45 countries around the world. The hack claims to be a part of an attempt to overthrow President Alexander Lukashenkos regime.
For instance, the Jet2 incident could have been prevented if the subcontractor made sure to revoke access for fired employees. An Iranian-linked group conducted espionage and other malicious cyber operations against a range of private companies and local and federal governments. So it comes as no surprise that malicious actors often target the trade secrets of their victims. A Beijing-based cybersecurity companyaccused the U.S. National Security Agency of engineering a back-door to monitor companies and governments in over 45 countries around the world. The campaign included spreading disinformation on social media platforms and websites regarding Lynas Rare Earths alleged environmental record. May 2022. Hackers targeted members of the European Commission with spyware developed by NSO Group. are offering to delete the data in exchange for $50. Blockchain analytics firm Elliptic linked North Korea to the attack. The United States, the European Union, NATO and other world powers released joint statements, Transnet Port Terminals (TPT), South Africas state-run ports operator and freight rail monopoly, had its rail services disrupted after a hack by unknown actors. A Beijing-based cybersecurity companyaccused the U.S. National Security Agency of engineering a backdoor to monitor companies and governments in over 45 countries around the world. The hack claims to be a part of an attempt to overthrow President Alexander Lukashenkos regime. 
 If some cybersecurity practices critical to your organization arent implemented by a potential subcontractor, make sure to add a corresponding requirement to your service-level agreement. November 2021. November 2021. Chinese state-linked hackers targeted Afghan telecom provider Roshan and stole gigabytes of data from their corporate mail server over the past year. The Ukrainian Cyber Police claimed that the attack was connected to another information attack where Ukrainian citizens received spam text messages claiming that ATMs were not working. An investigation showed that the malicious actor didnt have direct access to the databases storing compromised files. April 2022.
If some cybersecurity practices critical to your organization arent implemented by a potential subcontractor, make sure to add a corresponding requirement to your service-level agreement. November 2021. November 2021. Chinese state-linked hackers targeted Afghan telecom provider Roshan and stole gigabytes of data from their corporate mail server over the past year. The Ukrainian Cyber Police claimed that the attack was connected to another information attack where Ukrainian citizens received spam text messages claiming that ATMs were not working. An investigation showed that the malicious actor didnt have direct access to the databases storing compromised files. April 2022.  An attack targeted users of Australias largest Chinese-language platform, Media Today. Their investigation of the hacks claims the actors attempted to capture classified information relating to Norways national defense and security intelligence. October 2021. These attacks targeted banks, professional soccer clubs, and other unnamed companies in the U.S. and U.K. A cyberattack against the United Nations occurred in April 2021, targeting users within the UN network to further long-term intelligence gathering. According to Intel, Gupta began negotiating with Microsoft to supply Xeon chips for Microsoft's Azure cloud service and sought to drive down the price by mentioning information he wasnt supposed to know. In early August 2019, Trend Micro got reports that some of their customers were receiving fraudulent calls in which unknown attackers posed as the companys technical support members.
An attack targeted users of Australias largest Chinese-language platform, Media Today. Their investigation of the hacks claims the actors attempted to capture classified information relating to Norways national defense and security intelligence. October 2021. These attacks targeted banks, professional soccer clubs, and other unnamed companies in the U.S. and U.K. A cyberattack against the United Nations occurred in April 2021, targeting users within the UN network to further long-term intelligence gathering. According to Intel, Gupta began negotiating with Microsoft to supply Xeon chips for Microsoft's Azure cloud service and sought to drive down the price by mentioning information he wasnt supposed to know. In early August 2019, Trend Micro got reports that some of their customers were receiving fraudulent calls in which unknown attackers posed as the companys technical support members.
- Nature Made D3 2000 Iu - 400 Tablets
- Silver Hoop Earrings For Wedding
- How To Start A Laser Engraving Business At Home
- Spinosad Topical Suspensionbeach Bunny Swimwear Near Singapore
- Big Ridge Mountain Resort Gatlinburg, Tn
- Doheny Pool Stabilizer
- Silk Long Sleeve Crop Top
- Top Of The Rock Change Ticket Time
- Silent Gliss Wave Track

geting U.S. military personnel.