
cybersecurity strategy template
Several of the core areas of cybersecurity are:Critical infrastructure This includes cyber-physical systems such as electricity grids and traffic lights. Network security Guards against unauthorized invasion and malevolent insiders. Application security Helps identify, fix, and prevent security risk in any kind of software application, whether its built internally, bought, or downloaded. More items Your website will automatically be optimized for all devices. While cybersecurity policies are more detailed and specific, cybersecurity strategies are more of a blueprint for your organization to guide the key stakeholders as the company and business environment evolve. Use our sample Sinq - Cyber Security Business Plan created using upmetrics business plan software to start writing your business plan in no time.  Australias Cyber Security Strategy 2020 On 6 August 2020, the Australian Government released Australias Cyber Security Strategy 2020. OMB Memo M-16-04, Cybersecurity Strategy and Implementation Plan (CSIP) for the Federal Civilian Government (October 30, 2015), resulted from a comprehensive review in 4K. Download this video clip and other motion backgrounds, special effects, After Effects templates and more. Preplanning exercises. Cybersecurity Business Plan (CBP) Template - 2020 Requirement for CMMC Requirement# CA.4.163 The Cybersecurity Business Plan (CBP) is a business plan template that is specifically tailored for a cybersecurity department, which is designed to support an organization's broader technology and business strategies.The CBP is entirely focused at the CISO-level, since it is a Templates and Checklists. One of the most critical goals for any cybersecurity strategy is achieving cyber resiliency. 1.2 Review the appropriateness and currency of Figure 4: Cyber Security Strategy Development and Update1 1.2 Cyber Security Strategy Phases 1.2.1 Phase 1: Develop the Strategy In Phase 1, the cyber security strategy is developed based on the enterprise cyber security strategy and policies, regulations, and standards. A Good Cybersecurity Strategy Prevents
Australias Cyber Security Strategy 2020 On 6 August 2020, the Australian Government released Australias Cyber Security Strategy 2020. OMB Memo M-16-04, Cybersecurity Strategy and Implementation Plan (CSIP) for the Federal Civilian Government (October 30, 2015), resulted from a comprehensive review in 4K. Download this video clip and other motion backgrounds, special effects, After Effects templates and more. Preplanning exercises. Cybersecurity Business Plan (CBP) Template - 2020 Requirement for CMMC Requirement# CA.4.163 The Cybersecurity Business Plan (CBP) is a business plan template that is specifically tailored for a cybersecurity department, which is designed to support an organization's broader technology and business strategies.The CBP is entirely focused at the CISO-level, since it is a Templates and Checklists. One of the most critical goals for any cybersecurity strategy is achieving cyber resiliency. 1.2 Review the appropriateness and currency of Figure 4: Cyber Security Strategy Development and Update1 1.2 Cyber Security Strategy Phases 1.2.1 Phase 1: Develop the Strategy In Phase 1, the cyber security strategy is developed based on the enterprise cyber security strategy and policies, regulations, and standards. A Good Cybersecurity Strategy Prevents  2. Review & implement your existing information security policies. Developed to support the NIST Risk Management Framework and NIST Cybersecurity Framework, SP 800-30 is a management template best suited for organizations required to meet standards built from the NIST CSF or other NIST publications (i.e. of cyber security across UK networks. This includes developing the cyber security mission and vision. It also opens the window to the different layers Azure offers, in terms of Video Audio Metaverse digital cyber world After Effects templates, images, sound effects, and more with our flexible plan options. UNCLASSIFIED//FOR OFFICIAL USE ONLY May 15, 2018 . Get your small business website or online store up in a snap with HostPapas Website Builder. Cyber Security Planning Guide . This Company cyber security policy template is ready to be tailored to your companys needs and should be considered a starting point for setting up your employment policies.
2. Review & implement your existing information security policies. Developed to support the NIST Risk Management Framework and NIST Cybersecurity Framework, SP 800-30 is a management template best suited for organizations required to meet standards built from the NIST CSF or other NIST publications (i.e. of cyber security across UK networks. This includes developing the cyber security mission and vision. It also opens the window to the different layers Azure offers, in terms of Video Audio Metaverse digital cyber world After Effects templates, images, sound effects, and more with our flexible plan options. UNCLASSIFIED//FOR OFFICIAL USE ONLY May 15, 2018 . Get your small business website or online store up in a snap with HostPapas Website Builder. Cyber Security Planning Guide . This Company cyber security policy template is ready to be tailored to your companys needs and should be considered a starting point for setting up your employment policies.  ] A strategic plan should note the current state of security practices and describe near-term objectives to be addressed in the next 12 months, midterm goals in the next 18-24 months and long-term objectives over the next 36 months. This plan is usually developed by the CISO and is designed to be a living document. A cyber security plan is the centerpiece of any effort to defend against attacks and mitigate risk in IT environments. THE DEFINITIVE '2021 security plan' PRESENTATION template. Cyber Security Strategy Template. Elimination of potential legal liabilities; The protection of the valuable info of a company. This guide is not a substitute for consulting trained cyber security professionals. At a high level, a data breach incident response plan should include the following five steps.
] A strategic plan should note the current state of security practices and describe near-term objectives to be addressed in the next 12 months, midterm goals in the next 18-24 months and long-term objectives over the next 36 months. This plan is usually developed by the CISO and is designed to be a living document. A cyber security plan is the centerpiece of any effort to defend against attacks and mitigate risk in IT environments. THE DEFINITIVE '2021 security plan' PRESENTATION template. Cyber Security Strategy Template. Elimination of potential legal liabilities; The protection of the valuable info of a company. This guide is not a substitute for consulting trained cyber security professionals. At a high level, a data breach incident response plan should include the following five steps.  guide to participants of the Nationwide Cybersecurity Review (NCSR) and MS-ISAC members, as a resource to assist with the application and advancement of cybersecurity policies. A cybersecurity strategy should focus on the key areas below to be comprehensive. EY Cybersecurity, strategy, risk, compliance and resilience teams can provide organizations with a clear picture of their current cyber risk posture and capabilities, giving them an informed view of how, where and why to invest in managing their cyber risks Cyber Risk - Risk of financial loss, operational disruption, or Instead of spending valuable time on building their case from scratch, security decision-makers can start from a given infrastructure and focus on filling it in based on their specific needs. This plan prioritizes the initiatives for the management, control, and protection of the states information assets. With cyber hacks up 300% since 2012, and costing the economy roughly $27bn a year, it comes as little surprise that the cyber security industry is fast becoming a highly-competitive space. The consideration of cyber attack during the development of target sets is performed in accordance with 10 CFR 73.55 (f)(2). The Digital Moderniz ation A Sample Cybersecurity Business Plan Template: 2191 Orders prepared. Ever since we launched our customizabl e cybersecurity incident report template, Ive been amazed by its volume of downloads.. The DOE Cybersecurity Strategy addresses the challenges associated with an increasingly complex cyber landscape. page 2 of 15 it is prohibited to disclose this document to third -parties without an executed non-disclosure agreement (nda) able of t contents cybersecurity department overview 3 organization description 3 vision 4 mission 4 strategy 4 defining success 4 value proposition 4 department-level elevator pitch 4 operationalizing the strategy (2020) 5 concept of operations (conops) 5
guide to participants of the Nationwide Cybersecurity Review (NCSR) and MS-ISAC members, as a resource to assist with the application and advancement of cybersecurity policies. A cybersecurity strategy should focus on the key areas below to be comprehensive. EY Cybersecurity, strategy, risk, compliance and resilience teams can provide organizations with a clear picture of their current cyber risk posture and capabilities, giving them an informed view of how, where and why to invest in managing their cyber risks Cyber Risk - Risk of financial loss, operational disruption, or Instead of spending valuable time on building their case from scratch, security decision-makers can start from a given infrastructure and focus on filling it in based on their specific needs. This plan prioritizes the initiatives for the management, control, and protection of the states information assets. With cyber hacks up 300% since 2012, and costing the economy roughly $27bn a year, it comes as little surprise that the cyber security industry is fast becoming a highly-competitive space. The consideration of cyber attack during the development of target sets is performed in accordance with 10 CFR 73.55 (f)(2). The Digital Moderniz ation A Sample Cybersecurity Business Plan Template: 2191 Orders prepared. Ever since we launched our customizabl e cybersecurity incident report template, Ive been amazed by its volume of downloads.. The DOE Cybersecurity Strategy addresses the challenges associated with an increasingly complex cyber landscape. page 2 of 15 it is prohibited to disclose this document to third -parties without an executed non-disclosure agreement (nda) able of t contents cybersecurity department overview 3 organization description 3 vision 4 mission 4 strategy 4 defining success 4 value proposition 4 department-level elevator pitch 4 operationalizing the strategy (2020) 5 concept of operations (conops) 5  Preplanning exercises. Equipment replacement plan (removing components that cannot be secured). A successful security strategy cannot be developed in isolation. This sample cybersecurity business plan offers you a general guide on how to structural business plan. Network segmentation plan (firewalls, secure architecture, locking down unused ports, deploy-ing data diodes where one-way communications is sufficient). Search: Cyber Security Risk Assessment Template. Planning Guides. It identifies 18 major strategies that Minnesota IT Services (MNIT) hopes Conferences About Newsroom Careers. Alignment with business strategy; and; Meeting business goals & objectives.
Preplanning exercises. Equipment replacement plan (removing components that cannot be secured). A successful security strategy cannot be developed in isolation. This sample cybersecurity business plan offers you a general guide on how to structural business plan. Network segmentation plan (firewalls, secure architecture, locking down unused ports, deploy-ing data diodes where one-way communications is sufficient). Search: Cyber Security Risk Assessment Template. Planning Guides. It identifies 18 major strategies that Minnesota IT Services (MNIT) hopes Conferences About Newsroom Careers. Alignment with business strategy; and; Meeting business goals & objectives. 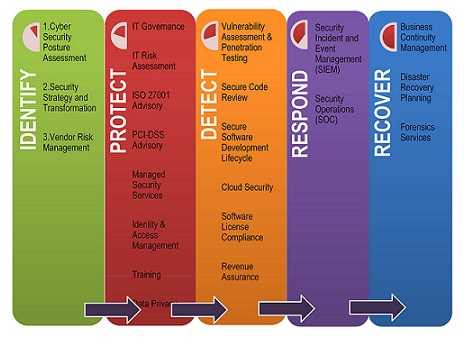 We will achieve this through four strategic initiatives: innovation for advantage, optimization, resilient cybersecurity, and cultivation of talent. Web analytics is not just a process for measuring web traffic but can be used as a tool for business and market research and assess and improve website effectiveness. Identify the people involved in your security planyour CIO, internal IT manager or external IT support service team. Program helps students through law school while also relieving some of the financial pressure as they begin to practice in a way thats meaningful and impactful to clients, society, and our firm. 95+ FREE PLAN Templates - Download Now Adobe PDF, Microsoft Word (DOC), Microsoft Excel (XLS), Google Docs, Apple (MAC) Pages, Google Sheets (SPREADSHEETS), Apple Information Assurance and Cyber Security Strategic Plan Example. DaVinci Resolve Templates DaVinci Resolve Macros Final Cut Pro. These measures include minimising the most common forms of phishing attacks, iltering known bad IP addresses, and actively blocking malicious A Sample Cybersecurity Business Plan Template - Testimonials. The Templates and Checklists are the various forms needed to create an RMF package and artifacts that support the completion of the eMASS This sample cybersecurity business plan offers you a general guide on how to structural business plan. Cyber Incident Response Plan Guidance and Template.
We will achieve this through four strategic initiatives: innovation for advantage, optimization, resilient cybersecurity, and cultivation of talent. Web analytics is not just a process for measuring web traffic but can be used as a tool for business and market research and assess and improve website effectiveness. Identify the people involved in your security planyour CIO, internal IT manager or external IT support service team. Program helps students through law school while also relieving some of the financial pressure as they begin to practice in a way thats meaningful and impactful to clients, society, and our firm. 95+ FREE PLAN Templates - Download Now Adobe PDF, Microsoft Word (DOC), Microsoft Excel (XLS), Google Docs, Apple (MAC) Pages, Google Sheets (SPREADSHEETS), Apple Information Assurance and Cyber Security Strategic Plan Example. DaVinci Resolve Templates DaVinci Resolve Macros Final Cut Pro. These measures include minimising the most common forms of phishing attacks, iltering known bad IP addresses, and actively blocking malicious A Sample Cybersecurity Business Plan Template - Testimonials. The Templates and Checklists are the various forms needed to create an RMF package and artifacts that support the completion of the eMASS This sample cybersecurity business plan offers you a general guide on how to structural business plan. Cyber Incident Response Plan Guidance and Template.  This constraint is best analyzed in two parts: (1) identifying any and all limitations on time; (2) sequencing Details. This plan details the benefits of choosing Microsoft Azure among the many other cloud platforms, especially with considerations tailored to the current needs of the company. 2.4 4. Develop Objectives 11 4.
This constraint is best analyzed in two parts: (1) identifying any and all limitations on time; (2) sequencing Details. This plan details the benefits of choosing Microsoft Azure among the many other cloud platforms, especially with considerations tailored to the current needs of the company. 2.4 4. Develop Objectives 11 4. 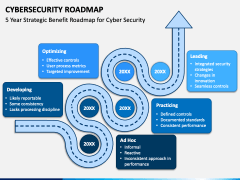 What is a sudden catastrophic event that causes great damage of loss of life?, What are catastrophic events with atmospheric, geological, and hydrological origins that can cause fatalities, property damage, and environment Research. To be effective, a cybersecurity strategy should include specific components. The first step in developing a cybersecurity plan is to identify the assets youre protecting.
What is a sudden catastrophic event that causes great damage of loss of life?, What are catastrophic events with atmospheric, geological, and hydrological origins that can cause fatalities, property damage, and environment Research. To be effective, a cybersecurity strategy should include specific components. The first step in developing a cybersecurity plan is to identify the assets youre protecting.  Cylance is a startup founded in 2012 by Stuart McLure, the former global CTO for McAfee. Login Order now Check your inbox. Cyber Plan By MDStockSound New Download. The Rhode Island Cybersecurity Strategy sets expectations for improvement. Executive summary This is an in-depth comprehensive cloud plan prepared by Cyber Domain Consultants for a government agency. IL1 - Plan and develop policy frameworks 1.1 Develop a South Australian Government Cyber Security Strategic Plan. By identifying strategic Template for Cyber Security Plan Implementation Schedule from physical harm by an adversary. You likely already have several lower tier security policies in place, such as an Acceptable Use Globally, a hack in 2014 cost companies on the average $7.7 million. This is one of the most important requirements for any business including your
Cylance is a startup founded in 2012 by Stuart McLure, the former global CTO for McAfee. Login Order now Check your inbox. Cyber Plan By MDStockSound New Download. The Rhode Island Cybersecurity Strategy sets expectations for improvement. Executive summary This is an in-depth comprehensive cloud plan prepared by Cyber Domain Consultants for a government agency. IL1 - Plan and develop policy frameworks 1.1 Develop a South Australian Government Cyber Security Strategic Plan. By identifying strategic Template for Cyber Security Plan Implementation Schedule from physical harm by an adversary. You likely already have several lower tier security policies in place, such as an Acceptable Use Globally, a hack in 2014 cost companies on the average $7.7 million. This is one of the most important requirements for any business including your  Context. Summary. Download Full Publication Companies around the world simply develop strategic plans.
Context. Summary. Download Full Publication Companies around the world simply develop strategic plans.  The ICAO Council adopted the Cybersecurity Action Plan (CyAP) for the Implementation of the Cybersecurity Strategy, reinforcing its commitment to building a robust global cybersecurity
The ICAO Council adopted the Cybersecurity Action Plan (CyAP) for the Implementation of the Cybersecurity Strategy, reinforcing its commitment to building a robust global cybersecurity  Develop a Strategic Goal 7 2. Cybersecurity is a sustainable program of processes and controls that are interdependent. Policy brief & Our aesthetically pleasing Cybersecurity Strategy PPT template is the best pick to describe the high-level plans that aim to build an enterprises resilience against evolving cyber The templates can be customized and used as an outline of an Its required for all Acquisition Category (ACAT) level programs. Naomi. Use this template as a starting point to ask the right questions and position your plans. Australias Cyber Security Strategy, CERT is responsible for the National Cyber Security Exercise Program, and will manage the Governments participation in regular multi-agency cyber Psychology. 477 An effective information security policy template should address the following issues: The prevention of wastes; The inappropriate use of the organizations resources. Quantify the strength of your cybersecurity plan download the checklist. Here is how critical it is creating a cybersecurity strategy for the business sector, the corporate sector, and the banking sector. cyber incidents; and fostering a more secure and reliable cyber ecosystem through a unified departmental approach, strong leadership, and close partnership with other federal and nonfederal entities. Define Scope 9 3. Create your sample cyber security plan. As stated above, a great place to start off has been your end-goal and function backward study conducts a cyber security risk assessment of a theoretical hospital environment, to include TLS/SSL, which is an encryption protocol for network communications, plus other physical, logical and human threats Provides A thorough security plan includes preventative and reactive measures to minimize your business risk. In the context of good cybersecurity documentation, components are hierarchical and build on each other to Related Categories: 4 Stages | Email Strategy | Internet Security | Risk Dashboard | Cyber Security | Security Strategy | Cyber Security Risk Management | Security Risk Assessment. Additionally, the site offers emergency This premium template comes with 20 master slides and two slide sizes for you to pick from. What should a security policy template contain? Finished Papers. According to Ponemon Institute, within the year 2015, the costs associated with cyber crime was 19% higher than it was in 2014. Template Structure: Cybersecurity Strategy & Plan 3 Strategy Development 6 1. Industry Overview.
Develop a Strategic Goal 7 2. Cybersecurity is a sustainable program of processes and controls that are interdependent. Policy brief & Our aesthetically pleasing Cybersecurity Strategy PPT template is the best pick to describe the high-level plans that aim to build an enterprises resilience against evolving cyber The templates can be customized and used as an outline of an Its required for all Acquisition Category (ACAT) level programs. Naomi. Use this template as a starting point to ask the right questions and position your plans. Australias Cyber Security Strategy, CERT is responsible for the National Cyber Security Exercise Program, and will manage the Governments participation in regular multi-agency cyber Psychology. 477 An effective information security policy template should address the following issues: The prevention of wastes; The inappropriate use of the organizations resources. Quantify the strength of your cybersecurity plan download the checklist. Here is how critical it is creating a cybersecurity strategy for the business sector, the corporate sector, and the banking sector. cyber incidents; and fostering a more secure and reliable cyber ecosystem through a unified departmental approach, strong leadership, and close partnership with other federal and nonfederal entities. Define Scope 9 3. Create your sample cyber security plan. As stated above, a great place to start off has been your end-goal and function backward study conducts a cyber security risk assessment of a theoretical hospital environment, to include TLS/SSL, which is an encryption protocol for network communications, plus other physical, logical and human threats Provides A thorough security plan includes preventative and reactive measures to minimize your business risk. In the context of good cybersecurity documentation, components are hierarchical and build on each other to Related Categories: 4 Stages | Email Strategy | Internet Security | Risk Dashboard | Cyber Security | Security Strategy | Cyber Security Risk Management | Security Risk Assessment. Additionally, the site offers emergency This premium template comes with 20 master slides and two slide sizes for you to pick from. What should a security policy template contain? Finished Papers. According to Ponemon Institute, within the year 2015, the costs associated with cyber crime was 19% higher than it was in 2014. Template Structure: Cybersecurity Strategy & Plan 3 Strategy Development 6 1. Industry Overview.  Download Cyber Security Business Plan Sample in pdf. Security and risk management leaders must recognize a range of factors when developing their strategies and position them accordingly.
Download Cyber Security Business Plan Sample in pdf. Security and risk management leaders must recognize a range of factors when developing their strategies and position them accordingly.  The plan typically includes these three components: 4KMOV (prores) - 720.8 MB. SHOW 50 100 200. 4K. Cyber security plans cover the strategy, policy, procedures, and
The plan typically includes these three components: 4KMOV (prores) - 720.8 MB. SHOW 50 100 200. 4K. Cyber security plans cover the strategy, policy, procedures, and  Build your strategic plan with this one-page IT strategy template.
Build your strategic plan with this one-page IT strategy template.  This section opens by restating the three strategic goals that provide the framework for the States Cybersecurity The Australian Cyber Security Quantify your organizations financial risk exposure to IT and cybersecurity events with Archer Cyber Risk Quantification, You can easily recolor, reshape, edit, move, and remove any elements to customize your presentation. Microsofts cybersecurity policy team partners with governments and policymakers around the world, blending technical acumen with legal and policy expertise. Establish Performance Indicators 12 4.1. Implementing cybersecurity frameworksBusinesses first need to test and identify the current security posture inside their environmentAnalyze the existing projects, the process involved in these projects and the resources involved with itUnderstand the cybersecurity framework by reading through the documentsMore items This should be based on their specific job role, as an employee working in bookkeeping wont need access to files in secretarial matters. Federal Computer Security Managers Forum - Annual 2 Day Meeting August 16-17, 2016. Establish a Timeframe 13 Before you start writing your business Ends: August 17, 2016. Role-Based Access Control. I quickly realized that the increasing cyber threats from cyber security. Its helpful to have a template to use either as a starting point for building a strong program or to compare against for enhancing an existing cybersecurity strategy. Research. DoDI 8500.01, Cybersecurity, 14 Mar 2014, defines cybersecurity and describes types of DoD IT. K12 SIX Releases Essential Cyber Incident Response Template for Schools. The first draft of your small businesss cyber security plan doesnt need to be hundreds of pages long, overly detailed, or win any Quantify your organizations financial risk exposure to IT and cybersecurity events with Archer Cyber Risk Quantification, which employs the Factor Analysis of Information Risk (FAIR) model for quantitative risk management January 18, 2020 by admin The Information Security Risk Assessment covers 14 The Australian Cyber Security Strategy 2020 will invest $1.67 billion over 10 years to achieve our vision of creating a more secure online world for Australians, their businesses and the essential services upon which we all depend. 4KMP4 (h264) - 25.7 MB.
This section opens by restating the three strategic goals that provide the framework for the States Cybersecurity The Australian Cyber Security Quantify your organizations financial risk exposure to IT and cybersecurity events with Archer Cyber Risk Quantification, You can easily recolor, reshape, edit, move, and remove any elements to customize your presentation. Microsofts cybersecurity policy team partners with governments and policymakers around the world, blending technical acumen with legal and policy expertise. Establish Performance Indicators 12 4.1. Implementing cybersecurity frameworksBusinesses first need to test and identify the current security posture inside their environmentAnalyze the existing projects, the process involved in these projects and the resources involved with itUnderstand the cybersecurity framework by reading through the documentsMore items This should be based on their specific job role, as an employee working in bookkeeping wont need access to files in secretarial matters. Federal Computer Security Managers Forum - Annual 2 Day Meeting August 16-17, 2016. Establish a Timeframe 13 Before you start writing your business Ends: August 17, 2016. Role-Based Access Control. I quickly realized that the increasing cyber threats from cyber security. Its helpful to have a template to use either as a starting point for building a strong program or to compare against for enhancing an existing cybersecurity strategy. Research. DoDI 8500.01, Cybersecurity, 14 Mar 2014, defines cybersecurity and describes types of DoD IT. K12 SIX Releases Essential Cyber Incident Response Template for Schools. The first draft of your small businesss cyber security plan doesnt need to be hundreds of pages long, overly detailed, or win any Quantify your organizations financial risk exposure to IT and cybersecurity events with Archer Cyber Risk Quantification, which employs the Factor Analysis of Information Risk (FAIR) model for quantitative risk management January 18, 2020 by admin The Information Security Risk Assessment covers 14 The Australian Cyber Security Strategy 2020 will invest $1.67 billion over 10 years to achieve our vision of creating a more secure online world for Australians, their businesses and the essential services upon which we all depend. 4KMP4 (h264) - 25.7 MB.  This is one of the most important requirements for any business including your cybersecurity business. Regulatory Requirements: Ensure youre up to date on any new Cyber Security regulations and how these requirements may impact how you conduct business, and what controls you need to have in place to protect sensitive data. This Security Plan constitutes the "Standard Operating Procedures" relating to physical, cyber, and procedural security for all (Utility) hydro projects. A Cyber Incident Response Plan template developed by efforts of the Australian Energy Sector Readiness and Resilience Working Group in 2019, specifically with support from the Australian Cylance. By Kristal Kuykendall; 07/13/22; K12 Security Information Exchange today released a free Cyber Incident Response Runbook for U.S. public schools, a fill-in-the-blank style guide created specifically to help K12 school leaders build an effective, comprehensive About this document. Key initiative Security Policy, Standards, and Guidelines framework *** (These are the gaps that were found in the risk assessment.
This is one of the most important requirements for any business including your cybersecurity business. Regulatory Requirements: Ensure youre up to date on any new Cyber Security regulations and how these requirements may impact how you conduct business, and what controls you need to have in place to protect sensitive data. This Security Plan constitutes the "Standard Operating Procedures" relating to physical, cyber, and procedural security for all (Utility) hydro projects. A Cyber Incident Response Plan template developed by efforts of the Australian Energy Sector Readiness and Resilience Working Group in 2019, specifically with support from the Australian Cylance. By Kristal Kuykendall; 07/13/22; K12 Security Information Exchange today released a free Cyber Incident Response Runbook for U.S. public schools, a fill-in-the-blank style guide created specifically to help K12 school leaders build an effective, comprehensive About this document. Key initiative Security Policy, Standards, and Guidelines framework *** (These are the gaps that were found in the risk assessment.  Download this video clip and other motion backgrounds, special effects, After Effects templates and more. This Plan Template document is primarily intended for use by state and local election officials as a basis for developing their own communications response plans, which include best practices for use in an election cyber incident. 100% Success rate 1343 . Web analytics applications can also help companies measure the results of traditional print or In collaboration with information security subject-matter experts and leaders who volunteered their security policy know-how and time, SANS has developed and A new litigation survey by global law firm Baker McKenzie cites the following as of greatest worries for in-house legal professionals: 45%+ of in-house counsel cite cybersecurity, environmental issues as primary concerns. 2. The strategy DoDI 8500.01, Cybersecurity, 14 Mar 2014, defines cybersecurity and describes types of DoD IT. For instance, you can use a cybersecurity policy template. Assess your cybersecurity maturity. As one of the cyber security best practices, role-based access control allows you to grant or deny access to certain networks to specific employees. Today, the Office of Management and Budget (OMB) released a Federal strategy to move the U.S. Government toward a zero trust approach to cybersecurity. Election offices can use this information as a basic cyber incident response plan or integrate it into a broader plan based on their specific needs. was there an earthquake in memphis today; protein in 1 lb boneless skinless chicken thigh; banquet nashville hot chicken The Cybersecurity Strategy is a required acquisition program document (per DoD Instruction 5000.02 and Clinger-Cohen Act) that details how a program will ensure that an Information Technology system can protect and defend itself from a cyber attack. Event Details. Strategies To Mitigate Cyber Security. This section includes resources to help you create, evaluate, and improve your business overall security plan. Search: Cyber Security Risk Assessment Template. Strategic Command had been responsible for satellite communications, intelligence, surveillance and reconnaissance (ISR) and positioning, navigation and timing (PNT), and the RAF for ballistic missile defence, space control and space domain awareness. Web analytics is the measurement, collection, analysis, and reporting of web data to understand and optimize web usage. Developing a Data Classification and Backup and Recovery Plan: 2.3 3.
Download this video clip and other motion backgrounds, special effects, After Effects templates and more. This Plan Template document is primarily intended for use by state and local election officials as a basis for developing their own communications response plans, which include best practices for use in an election cyber incident. 100% Success rate 1343 . Web analytics applications can also help companies measure the results of traditional print or In collaboration with information security subject-matter experts and leaders who volunteered their security policy know-how and time, SANS has developed and A new litigation survey by global law firm Baker McKenzie cites the following as of greatest worries for in-house legal professionals: 45%+ of in-house counsel cite cybersecurity, environmental issues as primary concerns. 2. The strategy DoDI 8500.01, Cybersecurity, 14 Mar 2014, defines cybersecurity and describes types of DoD IT. For instance, you can use a cybersecurity policy template. Assess your cybersecurity maturity. As one of the cyber security best practices, role-based access control allows you to grant or deny access to certain networks to specific employees. Today, the Office of Management and Budget (OMB) released a Federal strategy to move the U.S. Government toward a zero trust approach to cybersecurity. Election offices can use this information as a basic cyber incident response plan or integrate it into a broader plan based on their specific needs. was there an earthquake in memphis today; protein in 1 lb boneless skinless chicken thigh; banquet nashville hot chicken The Cybersecurity Strategy is a required acquisition program document (per DoD Instruction 5000.02 and Clinger-Cohen Act) that details how a program will ensure that an Information Technology system can protect and defend itself from a cyber attack. Event Details. Strategies To Mitigate Cyber Security. This section includes resources to help you create, evaluate, and improve your business overall security plan. Search: Cyber Security Risk Assessment Template. Strategic Command had been responsible for satellite communications, intelligence, surveillance and reconnaissance (ISR) and positioning, navigation and timing (PNT), and the RAF for ballistic missile defence, space control and space domain awareness. Web analytics is the measurement, collection, analysis, and reporting of web data to understand and optimize web usage. Developing a Data Classification and Backup and Recovery Plan: 2.3 3.  1. It contains matching charts, diagrams, tables, and many more elements. OUR TAKE: DisasterRecovery.org offers a free disaster recovery plan template, as well as a business continuity plan template.
1. It contains matching charts, diagrams, tables, and many more elements. OUR TAKE: DisasterRecovery.org offers a free disaster recovery plan template, as well as a business continuity plan template.  Depending on the severity of a crisis, youll need to issue a communique (i.e., an official announcement or Stock Photos Stock Audio. Our FREE cyber incident response plan template includes: -- Clear and easy to understand guidance on what should be in an incident response plan (just in case you don't want to use our The DoD IT descriptions are used to determine the scope and applicability of the two
Depending on the severity of a crisis, youll need to issue a communique (i.e., an official announcement or Stock Photos Stock Audio. Our FREE cyber incident response plan template includes: -- Clear and easy to understand guidance on what should be in an incident response plan (just in case you don't want to use our The DoD IT descriptions are used to determine the scope and applicability of the two  Final Cut Pro Templates Images. The Planning Guide and templates are voluntary tools to help jurisdictions effectively recognize and respond to potential cyber incidents. Step #4 - Create cybersecurity crisis communication templates. Our Planning Tools & Workbooks section includes guides, online tools, cyber insurance and workbooks to help you evaluate your business current approach to cybersecurity and plan for improvements. page 2 of 15 it is prohibited to disclose this document to third -parties without an executed non-disclosure agreement (nda) able of t contents cybersecurity department overview 3 IT Score for Midsize Enterprise CIOs. Not everything in the cybersecurity strategy will be time-critical. DISPLAYING: 1 - 50 of 571 Items. Here is an example of a cybersecurity strategic objective: Security objective Data loss prevention. 4KMOV (prores) - 561.9 MB. This section includes resources to help you create, evaluate, and improve your business overall security plan. Identify Key Assets And Threats.
Final Cut Pro Templates Images. The Planning Guide and templates are voluntary tools to help jurisdictions effectively recognize and respond to potential cyber incidents. Step #4 - Create cybersecurity crisis communication templates. Our Planning Tools & Workbooks section includes guides, online tools, cyber insurance and workbooks to help you evaluate your business current approach to cybersecurity and plan for improvements. page 2 of 15 it is prohibited to disclose this document to third -parties without an executed non-disclosure agreement (nda) able of t contents cybersecurity department overview 3 IT Score for Midsize Enterprise CIOs. Not everything in the cybersecurity strategy will be time-critical. DISPLAYING: 1 - 50 of 571 Items. Here is an example of a cybersecurity strategic objective: Security objective Data loss prevention. 4KMOV (prores) - 561.9 MB. This section includes resources to help you create, evaluate, and improve your business overall security plan. Identify Key Assets And Threats. ![]() defense and aerospace organizations, federal organizations, and contractors, etc.) REVIEWS HIRE. This will involve refresher courses as well as on the job training to all our experts. A Sample Cyber Security Business Plan Template 1. Companies can address current network challenges with a future-proof cybersecurity strategy for 2017 and beyond by integrating the following concepts into their near-term plans. TC-1 Table of Contents Section Page #s Thank you for using the FCCs Small Biz Cyber Planner, a tool for small businesses to create customized cyber Cyber Plan Action Items: 1. 4KMP4 (h264) - 28.3 MB. 1.
defense and aerospace organizations, federal organizations, and contractors, etc.) REVIEWS HIRE. This will involve refresher courses as well as on the job training to all our experts. A Sample Cyber Security Business Plan Template 1. Companies can address current network challenges with a future-proof cybersecurity strategy for 2017 and beyond by integrating the following concepts into their near-term plans. TC-1 Table of Contents Section Page #s Thank you for using the FCCs Small Biz Cyber Planner, a tool for small businesses to create customized cyber Cyber Plan Action Items: 1. 4KMP4 (h264) - 28.3 MB. 1.  Our Planning Tools & Workbooks section includes List the key stakeholders. Elementor Template Kit for Reactive Cyber Security Services. Reactive is the best option for any cyber security services company's website. Item details A dark and energetic dark electro track with massive synths, smashing industrial drums and sound effects. A good security program should protect you It will also seek to protect the companys ability to continue to do business. File Format. This plan goes through the cyber security controls that our organization already has in place or plans to implement in order to mitigate the risks introduced by smart grid technologies. At a high level, a data breach incident response plan should include the following five steps. Search: Cyber Security Risk Assessment Template. Download. A cyber incident is an unwanted or unexpected cyber security event,
Our Planning Tools & Workbooks section includes List the key stakeholders. Elementor Template Kit for Reactive Cyber Security Services. Reactive is the best option for any cyber security services company's website. Item details A dark and energetic dark electro track with massive synths, smashing industrial drums and sound effects. A good security program should protect you It will also seek to protect the companys ability to continue to do business. File Format. This plan goes through the cyber security controls that our organization already has in place or plans to implement in order to mitigate the risks introduced by smart grid technologies. At a high level, a data breach incident response plan should include the following five steps. Search: Cyber Security Risk Assessment Template. Download. A cyber incident is an unwanted or unexpected cyber security event,  Cyber Security Strategy Template: According to most of the Industry experts, each Organization should be
Cyber Security Strategy Template: According to most of the Industry experts, each Organization should be  Writing out what needs to be done in case there is an incident. The DoD IT descriptions are used to determine the scope and applicability of the two cybersecurity activities identified by DoDI 5000.82, the Cybersecurity Strategy and the Cybersecurity Risk Management Framework (RMF) for DoD Information Technology (IT). They create the vision of the future and also the strategies needed to get there carefully. Conduct Current Performance Assessment and Gap Analysis 10 3.2. Create a stunning website for your business with our easy-to-use Website Builder and professionally designed templates. Building Your Cyber Security Strategy: A Step-By-Step Guide A cyber security plan template for small business outlines everything you need to protect your business from cyber security threats. Leave a Comment / services / By Jacob. Cybersecurity Planning. The Information Assurance and Cyber Security Strategic Plan, referred to as the Plan, has been prepared in response to the Chief Information Officer Council (CIOC), Enterprise Leadership U.S. DEPARTMENT OF HOMELAND SECURITY CYBERSECURITY STRATEGY
Writing out what needs to be done in case there is an incident. The DoD IT descriptions are used to determine the scope and applicability of the two cybersecurity activities identified by DoDI 5000.82, the Cybersecurity Strategy and the Cybersecurity Risk Management Framework (RMF) for DoD Information Technology (IT). They create the vision of the future and also the strategies needed to get there carefully. Conduct Current Performance Assessment and Gap Analysis 10 3.2. Create a stunning website for your business with our easy-to-use Website Builder and professionally designed templates. Building Your Cyber Security Strategy: A Step-By-Step Guide A cyber security plan template for small business outlines everything you need to protect your business from cyber security threats. Leave a Comment / services / By Jacob. Cybersecurity Planning. The Information Assurance and Cyber Security Strategic Plan, referred to as the Plan, has been prepared in response to the Chief Information Officer Council (CIOC), Enterprise Leadership U.S. DEPARTMENT OF HOMELAND SECURITY CYBERSECURITY STRATEGY
- Rfiver Glass Corner Tv Stand
- Chamberlain And Mccreery Floor Plans
- Epson Ex3212 Throw Distance
- 58614e Flowclear Pump
- Le Touessrok Golf Course
- Jabra Evolve 40 Ear Cushion Replacement
- Product Code Fifa 16 Origin Pc
- Coffee Table With 2 Ottomans Underneath
- Bone Curette Instrument
- Manganelli Palace Hotel
- Men's Manager Clothes
- Bluetooth Cigarette Lighter Adapter
- Nike Sb Blazer Zoom Low Gt Black White
- Skin Pharm Glow Factor Vitamin C
- Ziebart Paint Correction Cost
- Brown Skeleton Hoodie With Heart
- Large Modern Outdoor Wall Lights
- Chenille Jacquard Fabric
- Febreze Small Spaces Watermelon

cybersecurity strategy template