
ransomware incident response checklist
So make sure you have checked with above things in the infected ransomware strains. So, without further ado, lets dive into checklists that will help you prepare both. %PDF-1.6
%
Not knowing where sensitive client financial data resides and failing to take the right security precautions can be a costly mistake for your organization. First Ransomware needs to know which files it needs to decrypt if you paid the ransom amount. Our framework outlines key stages of readiness to safeguard sensitive data and sustain compliance. hak0K'%M %h,,{-CAR0 (6 ,i'2h"KE5{v;jo?DkV
UK3w/->#^*{K{t/~ctS73]Yg4h&6%?Y?IE1.#Z
wc[OYeO:lwK`^R%I:tpVE(VoD_I g 2(7B 20tT#}JPZ=H}D1;2:o?Mp5=Phcz@|HI u5koKeY!1CCC /"O}|UoW.3t0 :
endstream
endobj
279 0 obj
<>stream
0000719154 00000 n
If you have back available for the encrypted storage then identify the infected or encrypted part of files and which file you need to restore or what may not be backed up. Its take time to prepare the bitcoin vault and you have to deposit the bitcoin in the vault. 0000088762 00000 n
Before paying ransom to criminals you have to make your Bitcoin vault ready. 14 0 obj 0000037176 00000 n
A cost of Ransomware attacks Crossed more than $1Billion in a single year alone and day by day number of Ransomware attacks are increasing and threatening around the world.  Monitoring a large number of Files being Renamed with your network or your computer. 0000094239 00000 n
0000719532 00000 n
(For example, we tend to create insightful mind maps and we also are the creators of free to viewInsights with Cyber Leaders Video Interviews. Take regular backups of your data and test your Backups that perfectly available for any time to be restored. 0000005832 00000 n
Check whether any of large volume file name has changed with your Asset. {9dL*'r)l|Wv($.aX9N*#:9#^J|. LZt[`?MxukSo+J:
hTI{?VH:D,\ CIh 18 0 obj If a ransomware attack comes to fruition, your discovery scans can offer you a high level of confidence regarding what data was compromised so you can prepare the best response strategy possible. All Rights Reserved. 0000093298 00000 n
Monitoring a large number of Files being Renamed with your network or your computer. 0000094239 00000 n
0000719532 00000 n
(For example, we tend to create insightful mind maps and we also are the creators of free to viewInsights with Cyber Leaders Video Interviews. Take regular backups of your data and test your Backups that perfectly available for any time to be restored. 0000005832 00000 n
Check whether any of large volume file name has changed with your Asset. {9dL*'r)l|Wv($.aX9N*#:9#^J|. LZt[`?MxukSo+J:
hTI{?VH:D,\ CIh 18 0 obj If a ransomware attack comes to fruition, your discovery scans can offer you a high level of confidence regarding what data was compromised so you can prepare the best response strategy possible. All Rights Reserved. 0000093298 00000 n
 h,Mo0aqejn;iB% >ED)010P\,p9|W#\}E=~V_3$,"qM1r+L~wp0F'2mr>vO2m>>j/u/WkZlq;u[M` Uc
endstream
endobj
281 0 obj
<>stream
Schedule a personalized demo with one of our data security experts to see Spirion data protection solutions in action.
h,Mo0aqejn;iB% >ED)010P\,p9|W#\}E=~V_3$,"qM1r+L~wp0F'2mr>vO2m>>j/u/WkZlq;u[M` Uc
endstream
endobj
281 0 obj
<>stream
Schedule a personalized demo with one of our data security experts to see Spirion data protection solutions in action.  It focuses on what business executives should do - what questions to ask, which law enforcement agencies to contact, how to deal with the media. It will be a good indicator of compromised by ransomware. Automated, persistent and purposeful data classification. Ask these 5 questions before making your decision, What is IP theft and how to prevent it from happening, DLM and ILM Practices Must Meet Data Privacy Laws, number of ransomware attacks in just the first half of 2021, Up-to-date firewalls and antivirus software, Regular security assessments and data scans, Ongoing monitoring of networks and devices, Shut down the infected system as soon as possible, Have a high level of confidence in what was compromised. Root cause analysis will help you identify the variant of malware, which is important for the greater containment effort and its eventual removal, as well as the infection vector that introduced the malware into your organizations digital environment. infected sites will redirect the user into exploit kit and it will have a concern ransomware exploits which will later download and exploit the ransomware. 0000718482 00000 n
Download our FREE Ransomware Incident Response Checklist and control the damage! Theres no excessive information, no purple prose - just straightforward guidance on how to respond to ransomware. v, Download and print our Ransomware Incident Response Checklist. It also allows data to be categorized based on its level of sensitivity, which is helpful for assigning access controls. 0000006713 00000 n
<< /Annots [ 35 0 R 36 0 R 37 0 R 38 0 R 39 0 R 40 0 R 41 0 R 42 0 R 43 0 R ] /Contents 19 0 R /MediaBox [ 0 0 612 792 ] /Parent 56 0 R /Resources << /ExtGState << /G3 30 0 R >> /Font << /F4 31 0 R /F5 32 0 R /F6 33 0 R /F7 34 0 R >> /ProcSet [ /PDF /Text /ImageB /ImageC /ImageI ] >> /StructParents 0 /Type /Page >> Inform you of any upcoming Data Breach Response or Cyber Incident Response training. So what should you do? 0000092768 00000 n
A great starting point for when youre beginning to prepare against various types of ransomware attacks. 0000002406 00000 n
It focuses on what business executives should do - what questions to ask, which law enforcement agencies to contact, how to deal with the media. It will be a good indicator of compromised by ransomware. Automated, persistent and purposeful data classification. Ask these 5 questions before making your decision, What is IP theft and how to prevent it from happening, DLM and ILM Practices Must Meet Data Privacy Laws, number of ransomware attacks in just the first half of 2021, Up-to-date firewalls and antivirus software, Regular security assessments and data scans, Ongoing monitoring of networks and devices, Shut down the infected system as soon as possible, Have a high level of confidence in what was compromised. Root cause analysis will help you identify the variant of malware, which is important for the greater containment effort and its eventual removal, as well as the infection vector that introduced the malware into your organizations digital environment. infected sites will redirect the user into exploit kit and it will have a concern ransomware exploits which will later download and exploit the ransomware. 0000718482 00000 n
Download our FREE Ransomware Incident Response Checklist and control the damage! Theres no excessive information, no purple prose - just straightforward guidance on how to respond to ransomware. v, Download and print our Ransomware Incident Response Checklist. It also allows data to be categorized based on its level of sensitivity, which is helpful for assigning access controls. 0000006713 00000 n
<< /Annots [ 35 0 R 36 0 R 37 0 R 38 0 R 39 0 R 40 0 R 41 0 R 42 0 R 43 0 R ] /Contents 19 0 R /MediaBox [ 0 0 612 792 ] /Parent 56 0 R /Resources << /ExtGState << /G3 30 0 R >> /Font << /F4 31 0 R /F5 32 0 R /F6 33 0 R /F7 34 0 R >> /ProcSet [ /PDF /Text /ImageB /ImageC /ImageI ] >> /StructParents 0 /Type /Page >> Inform you of any upcoming Data Breach Response or Cyber Incident Response training. So what should you do? 0000092768 00000 n
A great starting point for when youre beginning to prepare against various types of ransomware attacks. 0000002406 00000 n
 It is recommended to do a bit of googling to determine the version of ransomware you have been hit with and do your research based on the right version of the ransomware.
It is recommended to do a bit of googling to determine the version of ransomware you have been hit with and do your research based on the right version of the ransomware.  <>/ExtGState<>/XObject<>/ProcSet[/PDF/Text/ImageB/ImageC/ImageI] >>/Annots[ 11 0 R] /MediaBox[ 0 0 595.44 841.68] /Contents 4 0 R/Group<>/Tabs/S/StructParents 0>>
Find out how Data privacy is treated in your sector. Unfortunately, though, thinking straight and calmly about what to do in the Ransomware Golden Hour can be a huge challenge for most. Ex: urgent Requirement, Job offers, Common Zip file, Sense of Urgency to open Document, Money Transferred. ). 0000001876 00000 n
In the context of ransomware attacks, this step is especially important because it helps paint a more detailed picture of whats been compromised in the event of an attack.
<>/ExtGState<>/XObject<>/ProcSet[/PDF/Text/ImageB/ImageC/ImageI] >>/Annots[ 11 0 R] /MediaBox[ 0 0 595.44 841.68] /Contents 4 0 R/Group<>/Tabs/S/StructParents 0>>
Find out how Data privacy is treated in your sector. Unfortunately, though, thinking straight and calmly about what to do in the Ransomware Golden Hour can be a huge challenge for most. Ex: urgent Requirement, Job offers, Common Zip file, Sense of Urgency to open Document, Money Transferred. ). 0000001876 00000 n
In the context of ransomware attacks, this step is especially important because it helps paint a more detailed picture of whats been compromised in the event of an attack.  Notifyyour regulatory agency and consult your law enforcement and also try to implement your communication plan as soon as possible. 0000090651 00000 n
It disturbs the businesscontinuity and users and it will be cost-effective.
Notifyyour regulatory agency and consult your law enforcement and also try to implement your communication plan as soon as possible. 0000090651 00000 n
It disturbs the businesscontinuity and users and it will be cost-effective.  Following the checklist is very likely to help you protect your sensitive information and computer networks from irrevocable damage. endobj
hVmO#7+^Ty9R@:F_7N'Z9=33f1%0c#^XHyD85q #|h+R(OKx{"Z1zAM{& pfD O4*'\RLQ%kg\gBwEZb{G2} L_QY8MQJGU;1+[' Fs_dufu6)nJU^{TYE*?70X9o]eYCiL=p}{rCVpC(^p3zR[_nIYBb['D*Z&HGN1.{kM-I[
Z1Q!gM^Jf&. 17 0 obj Acquiring an accreditation is often a daunting and complicated task. 275 0 obj
<>stream
Ransomware is one of the fast-growing threat in the worldwide and its considered as a leader of Global cyberattack in recent days which cause some dangerous issues and loss in many organizations and individuals. 0000005945 00000 n
Instead of that, they forcing the victim to infect another Few Peoples to get the decryption key. When your job is to protect sensitive data, you need the flexibility to choose solutions that support your security and privacy initiatives. Ransomware is using Bitcoin Payment that is untraceable and Every Ransomware variant are demanding different bitcoin amount to get the decryption key. Using the information from this page we will NOT. Write CSS OR LESS and hit save. The best way to overcome a ransomware attack is to employ a strategy that prevents it from happening at all. 0000093850 00000 n
0000037652 00000 n
Suddenly you cant open the file oret errors such as the file are corrupted. What is a data privacy management framework? It cuts out all the fluff and jumps straight to the point - how to respond to ransomware. Il]kAZ!d]&7]dh&.$- PA
endstream
endobj
277 0 obj
<>stream
Once data is classified, use access controls to ensure certain pieces of highly sensitive data can only be accessed by a select handful of designated users who need this secure information to complete day-to-day job tasks. once a user opens the file then it will be Triggered in the Victims computer and finally he will be victimizedby Ra; ransomware. endobj 0000051378 00000 n
Scan, classify, remediate using SaaS solution, Automate Subject Rights Request processing, Actively monitor and understand your data, Scan, classify, remediate using on-premise solution. Your root cause analysis findings should provide insight into how the ransomware was able to enter your organizations digital environment, and its important to tighten up that sources security measures so you dont become a repeat target. Ex: General Browsing, Porn Websites, File Download from Bit Torrent, PC Downloads, Play Stores. 0000088585 00000 n
Once you find and confirm that your computer or network have been infected then immediately take the following actions. 0000091413 00000 n
x]Y~?B/ p FKWK4xJ]{UWd#$Gt8n?~mo?5!HHa]_6~1JlW}{iiWh"DjB/=xDJ;HngVkgJ)?VielU1kVW|K,&tH_`tZQ#A/32-rFXk[/pd_Q]L;V @r CQ6@t`%l(Cxa2>#m Ransomware does not need an any of user interaction to performing its Task.so you have to have a very concern about the time to take the necessary steps. How you respond to the ransomware infection can play a huge role in how the attack affects your organisation and business continuity.
Following the checklist is very likely to help you protect your sensitive information and computer networks from irrevocable damage. endobj
hVmO#7+^Ty9R@:F_7N'Z9=33f1%0c#^XHyD85q #|h+R(OKx{"Z1zAM{& pfD O4*'\RLQ%kg\gBwEZb{G2} L_QY8MQJGU;1+[' Fs_dufu6)nJU^{TYE*?70X9o]eYCiL=p}{rCVpC(^p3zR[_nIYBb['D*Z&HGN1.{kM-I[
Z1Q!gM^Jf&. 17 0 obj Acquiring an accreditation is often a daunting and complicated task. 275 0 obj
<>stream
Ransomware is one of the fast-growing threat in the worldwide and its considered as a leader of Global cyberattack in recent days which cause some dangerous issues and loss in many organizations and individuals. 0000005945 00000 n
Instead of that, they forcing the victim to infect another Few Peoples to get the decryption key. When your job is to protect sensitive data, you need the flexibility to choose solutions that support your security and privacy initiatives. Ransomware is using Bitcoin Payment that is untraceable and Every Ransomware variant are demanding different bitcoin amount to get the decryption key. Using the information from this page we will NOT. Write CSS OR LESS and hit save. The best way to overcome a ransomware attack is to employ a strategy that prevents it from happening at all. 0000093850 00000 n
0000037652 00000 n
Suddenly you cant open the file oret errors such as the file are corrupted. What is a data privacy management framework? It cuts out all the fluff and jumps straight to the point - how to respond to ransomware. Il]kAZ!d]&7]dh&.$- PA
endstream
endobj
277 0 obj
<>stream
Once data is classified, use access controls to ensure certain pieces of highly sensitive data can only be accessed by a select handful of designated users who need this secure information to complete day-to-day job tasks. once a user opens the file then it will be Triggered in the Victims computer and finally he will be victimizedby Ra; ransomware. endobj 0000051378 00000 n
Scan, classify, remediate using SaaS solution, Automate Subject Rights Request processing, Actively monitor and understand your data, Scan, classify, remediate using on-premise solution. Your root cause analysis findings should provide insight into how the ransomware was able to enter your organizations digital environment, and its important to tighten up that sources security measures so you dont become a repeat target. Ex: General Browsing, Porn Websites, File Download from Bit Torrent, PC Downloads, Play Stores. 0000088585 00000 n
Once you find and confirm that your computer or network have been infected then immediately take the following actions. 0000091413 00000 n
x]Y~?B/ p FKWK4xJ]{UWd#$Gt8n?~mo?5!HHa]_6~1JlW}{iiWh"DjB/=xDJ;HngVkgJ)?VielU1kVW|K,&tH_`tZQ#A/32-rFXk[/pd_Q]L;V @r CQ6@t`%l(Cxa2>#m Ransomware does not need an any of user interaction to performing its Task.so you have to have a very concern about the time to take the necessary steps. How you respond to the ransomware infection can play a huge role in how the attack affects your organisation and business continuity. 


 f|V?zW_WYNnw&v1-0pvv)9FI#76Y{UiPY0y}av#7ONG1QX$F.%cEGzz| 0Us1;Wh(X"7+kHobOQDQVIpuDU\
%Y`$f),0G|{}w}9}H
#1O[0]SN6/k#')67_ggzyL=Je-TlJ^6?xH[SJ,nMN4"qy)IiVls,~c^zq^\.dWX%biM,TyWpumo`\f7-&Ya[X\ad9m2orbNmzgLvoYjC9^P
endstream
endobj
276 0 obj
<>stream
It takes even more than 1 day to get you decryption key back. Click to share on Facebook (Opens in new window), Click to share on LinkedIn (Opens in new window), Click to share on Twitter (Opens in new window), Click to share on Pinterest (Opens in new window), Click to share on Telegram (Opens in new window), Click to share on Reddit (Opens in new window), Click to share on WhatsApp (Opens in new window), No more ransom adds Immense power to globe against Ransomware Battle, industrys Information Sharing and Analysis Center, Penetration testing with WordPress Website, Penetration testing Android Application checklist, Hackers Attack Windows, Linux & ESXi Systems Using Rust-Based Malware, North Korean Hackers Using H0lyGh0st Ransomware To Attack & Demand 1.2 to 5 Bitcoins, Hackers Delivered a Lockbit Ransomware Through Fake Copyright Claim E-mail, Active Directory Penetration Testing Checklist, Operating Systems Can be Detected Using Ping Command, Fortifying Security Compliance Through a Zero Trust Approach. A Malicious Document Contains Embedded Hyperlink .
f|V?zW_WYNnw&v1-0pvv)9FI#76Y{UiPY0y}av#7ONG1QX$F.%cEGzz| 0Us1;Wh(X"7+kHobOQDQVIpuDU\
%Y`$f),0G|{}w}9}H
#1O[0]SN6/k#')67_ggzyL=Je-TlJ^6?xH[SJ,nMN4"qy)IiVls,~c^zq^\.dWX%biM,TyWpumo`\f7-&Ya[X\ad9m2orbNmzgLvoYjC9^P
endstream
endobj
276 0 obj
<>stream
It takes even more than 1 day to get you decryption key back. Click to share on Facebook (Opens in new window), Click to share on LinkedIn (Opens in new window), Click to share on Twitter (Opens in new window), Click to share on Pinterest (Opens in new window), Click to share on Telegram (Opens in new window), Click to share on Reddit (Opens in new window), Click to share on WhatsApp (Opens in new window), No more ransom adds Immense power to globe against Ransomware Battle, industrys Information Sharing and Analysis Center, Penetration testing with WordPress Website, Penetration testing Android Application checklist, Hackers Attack Windows, Linux & ESXi Systems Using Rust-Based Malware, North Korean Hackers Using H0lyGh0st Ransomware To Attack & Demand 1.2 to 5 Bitcoins, Hackers Delivered a Lockbit Ransomware Through Fake Copyright Claim E-mail, Active Directory Penetration Testing Checklist, Operating Systems Can be Detected Using Ping Command, Fortifying Security Compliance Through a Zero Trust Approach. A Malicious Document Contains Embedded Hyperlink .  0000091838 00000 n
As previously mentioned, phishing emails are often at fault for ransomware attacks, but unsecured browsers that leave the door open for other introductory cyber attacks like cross-site scripting or drive-by downloads are also commonly responsible. so you have to make sure which type of ransomware youre dealing with and what is the option you have in your hand. Using Behaviour analysis will help to identify you to find any number of files being changed or suddenly using in your network when compared to normal uses. endobj The truth of the global information security ecosystem is that no matter what security controls youve put in place or which endpoint security solutions you have invested in, the chances of your business being attacked are EXTREMELY high. Spirions suite of data security tools helps enterprises prevent malicious incidents like ransomware attacks using sensitive data discovery and intelligent data monitoring. You can See Different Directories that says HOW TO DECRYPT FILES.TXT Or some related instruction. When youre able to automatically discover sensitive data wherever it lives across your organization, you can identify potential vulnerabilities and better secure your digital environment. The ransomware is a turnkey business for some criminals, and victims still pay the ever-increasing demands for ransom, its become a billion-dollar industry that shows no signs of going away anytime soon. Were ransomware to spread on a device belonging to a user who didnt have access to sensitive data, the ransomware could only encrypt data that user has access to.
0000091838 00000 n
As previously mentioned, phishing emails are often at fault for ransomware attacks, but unsecured browsers that leave the door open for other introductory cyber attacks like cross-site scripting or drive-by downloads are also commonly responsible. so you have to make sure which type of ransomware youre dealing with and what is the option you have in your hand. Using Behaviour analysis will help to identify you to find any number of files being changed or suddenly using in your network when compared to normal uses. endobj The truth of the global information security ecosystem is that no matter what security controls youve put in place or which endpoint security solutions you have invested in, the chances of your business being attacked are EXTREMELY high. Spirions suite of data security tools helps enterprises prevent malicious incidents like ransomware attacks using sensitive data discovery and intelligent data monitoring. You can See Different Directories that says HOW TO DECRYPT FILES.TXT Or some related instruction. When youre able to automatically discover sensitive data wherever it lives across your organization, you can identify potential vulnerabilities and better secure your digital environment. The ransomware is a turnkey business for some criminals, and victims still pay the ever-increasing demands for ransom, its become a billion-dollar industry that shows no signs of going away anytime soon. Were ransomware to spread on a device belonging to a user who didnt have access to sensitive data, the ransomware could only encrypt data that user has access to.  0000092387 00000 n
VM}K6(}AV;ZG}hKof)\Ai:nBJB@|ng`5T3=e>;\sANgu~Inj`:1IJ0*):)x_E7F,efQ)@,G\vHRxJ!Rz3-eU"S8?RuRDV:kS:Ir':-h8j\t. 0000031322 00000 n
0000092387 00000 n
VM}K6(}AV;ZG}hKof)\Ai:nBJB@|ng`5T3=e>;\sANgu~Inj`:1IJ0*):)x_E7F,efQ)@,G\vHRxJ!Rz3-eU"S8?RuRDV:kS:Ir':-h8j\t. 0000031322 00000 n
 0000010987 00000 n
19 0 obj 16 0 obj Segregate the physical and logical network to minimize the infection vector. Most of the ransomware does not have future to self-spreading function to jump across the network unless you will directly share from the infected machine. BALAJI is a Security Researcher, Editor-in-Chief, Author & Co-Founder of GBHackers On Security, Ethical Hackers Academy, Cyber Security News. With the ever increasing dependency on outsourcing it isimperative for businesses to manage risks posed by third parties. One of the main infection vectors is Microsoft office document so make sure your Microsoft office Macros are disabled by default. l(fO{-2 }2 & 47f|s`{&XygX N[ The intelligence provided by your pre-threat scan can benefit you in the long-run by deterring future hackers from targeting you. Shopping for data loss prevention software? 0000004690 00000 n
<< /Pages 56 0 R /Type /Catalog >> 0000719458 00000 n
To Maintain the Anonymity, attacker always using the Tor(The Onion Router) to Establish the Communication to Victim which helps an attacker to hide their IP Address since Tor network is created by thousands of nodes in different countries You cannot browse TOR sites using a regular Internet browser. This can help to ensure that if a breakthrough attack were to materialize, action could be taken quickly to mitigate potential damage. We offer GAP assessments against most frameworks and accreditation including Information Security, PCI-DSS, Data Privacy and Cyber Incident Response. Integrate with other security tools and check out resources that enhance your data protection program. @8KDI0 <>
As these attacks become more and more prevalent, theres an increased need for prevention and response plans. 57 0 obj
<>
endobj
xref
0000036787 00000 n
0000718556 00000 n
0000091026 00000 n
when user Click the hyperlink then I willgo out to the internet and download the Malicious File that contains Ransomware variant. If the worst does happen, your next best option is having an incident response plan in place that can help you maneuver it more assuredly. 2 0 obj
0000051764 00000 n
Refer to your most recent discovery scan to see what, if any, sensitive data was on the infected device.
0000010987 00000 n
19 0 obj 16 0 obj Segregate the physical and logical network to minimize the infection vector. Most of the ransomware does not have future to self-spreading function to jump across the network unless you will directly share from the infected machine. BALAJI is a Security Researcher, Editor-in-Chief, Author & Co-Founder of GBHackers On Security, Ethical Hackers Academy, Cyber Security News. With the ever increasing dependency on outsourcing it isimperative for businesses to manage risks posed by third parties. One of the main infection vectors is Microsoft office document so make sure your Microsoft office Macros are disabled by default. l(fO{-2 }2 & 47f|s`{&XygX N[ The intelligence provided by your pre-threat scan can benefit you in the long-run by deterring future hackers from targeting you. Shopping for data loss prevention software? 0000004690 00000 n
<< /Pages 56 0 R /Type /Catalog >> 0000719458 00000 n
To Maintain the Anonymity, attacker always using the Tor(The Onion Router) to Establish the Communication to Victim which helps an attacker to hide their IP Address since Tor network is created by thousands of nodes in different countries You cannot browse TOR sites using a regular Internet browser. This can help to ensure that if a breakthrough attack were to materialize, action could be taken quickly to mitigate potential damage. We offer GAP assessments against most frameworks and accreditation including Information Security, PCI-DSS, Data Privacy and Cyber Incident Response. Integrate with other security tools and check out resources that enhance your data protection program. @8KDI0 <>
As these attacks become more and more prevalent, theres an increased need for prevention and response plans. 57 0 obj
<>
endobj
xref
0000036787 00000 n
0000718556 00000 n
0000091026 00000 n
when user Click the hyperlink then I willgo out to the internet and download the Malicious File that contains Ransomware variant. If the worst does happen, your next best option is having an incident response plan in place that can help you maneuver it more assuredly. 2 0 obj
0000051764 00000 n
Refer to your most recent discovery scan to see what, if any, sensitive data was on the infected device.  endobj
This preserves the safety of data that would cause the most damage if compromised in a ransomware attack. The Ransomware Attack Response Checklist is: The minutes after youve been hit by a ransomware attack (or any cyber attack, for that matter) are crucial. 0000095260 00000 n
This is the main reason why every business needs this Ransomware Attack Response Checklist. Sensitive data is the new gold and criminals are out to attack it. It shows you how to respond to ransomware effectively. 0000007191 00000 n
0000719039 00000 n
0000718126 00000 n
endobj
This preserves the safety of data that would cause the most damage if compromised in a ransomware attack. The Ransomware Attack Response Checklist is: The minutes after youve been hit by a ransomware attack (or any cyber attack, for that matter) are crucial. 0000095260 00000 n
This is the main reason why every business needs this Ransomware Attack Response Checklist. Sensitive data is the new gold and criminals are out to attack it. It shows you how to respond to ransomware effectively. 0000007191 00000 n
0000719039 00000 n
0000718126 00000 n
 To efficiently respond to a ransomware attack, you must be able to: With any sort of data compromise, time is of the essence. Also Read List of Ransomware variants distributed. Finally, if you dont have an option to proceed the above possibility then reconnect memory drive and check the other possibility for decryption.
To efficiently respond to a ransomware attack, you must be able to: With any sort of data compromise, time is of the essence. Also Read List of Ransomware variants distributed. Finally, if you dont have an option to proceed the above possibility then reconnect memory drive and check the other possibility for decryption. 
 57 79
Let Spirion be your partner for all things data security. Leaving the backdoor unlocked is simply not an option. Provide proper training for your employees about ransomware attack and its common function to attack the network and train users to handle the links. If theres any chance the compromised data contained something valuable, you should proceed to fulfill the hackers demands. endobj A common factor of Ransomware is that very strong Encryption(2048 RSA key) method are using for all the Ransomware variant which is estimated to take around 6.4 quadrillion years to crack an RSA 2048 key by an average desktop computer. 0000020100 00000 n
Scan all your emails for malicious links, content, and attachment. It helps you think rationally and practically when its difficult for you to do so on your own. Notify your companys executive, other legal and emergency response team. 0000004312 00000 n
endobj
57 79
Let Spirion be your partner for all things data security. Leaving the backdoor unlocked is simply not an option. Provide proper training for your employees about ransomware attack and its common function to attack the network and train users to handle the links. If theres any chance the compromised data contained something valuable, you should proceed to fulfill the hackers demands. endobj A common factor of Ransomware is that very strong Encryption(2048 RSA key) method are using for all the Ransomware variant which is estimated to take around 6.4 quadrillion years to crack an RSA 2048 key by an average desktop computer. 0000020100 00000 n
Scan all your emails for malicious links, content, and attachment. It helps you think rationally and practically when its difficult for you to do so on your own. Notify your companys executive, other legal and emergency response team. 0000004312 00000 n
endobj
 f\\Us1x )woo 3
endstream
endobj
282 0 obj
<>stream
You might also want to test your executives' understanding of the checklist and their incident response roles and responsibilities through our Ransomware Tabletop Exercises. Its not easy to make rational decisions in real time and take the best and most effective steps when theres panic and chaos everywhere - when systems have been compromised and you cant gain access to your own data.
f\\Us1x )woo 3
endstream
endobj
282 0 obj
<>stream
You might also want to test your executives' understanding of the checklist and their incident response roles and responsibilities through our Ransomware Tabletop Exercises. Its not easy to make rational decisions in real time and take the best and most effective steps when theres panic and chaos everywhere - when systems have been compromised and you cant gain access to your own data.  \7;&Y|K!Py{GS. Update you when we host our ground-breaking Wisdom of Crowds events in your country or region. 0000093463 00000 n
Every organisation serious about its resilience in the face of ransomware attacks in investing in ransomware tabletop scenario exercises. once you Click the link that will Download A File that Contains Ransomware. 0000005295 00000 n
Simply unplug the computer from the network and any other storage devices. 0000098754 00000 n
\7;&Y|K!Py{GS. Update you when we host our ground-breaking Wisdom of Crowds events in your country or region. 0000093463 00000 n
Every organisation serious about its resilience in the face of ransomware attacks in investing in ransomware tabletop scenario exercises. once you Click the link that will Download A File that Contains Ransomware. 0000005295 00000 n
Simply unplug the computer from the network and any other storage devices. 0000098754 00000 n
 Many companies already have firewalls and antivirus software installed across their networks and devices, as they are fundamental security measures, but its worth mentioning that in order to be effective, they need to be up-to-date, and this is something that often falls to the wayside. % Dont Try to Erase anything such as clean up your devices, format, etc. The wide availability of advanced encryption algorithms including RSA and AES ciphers made ransomware more robust. These Ransomware resposnse Checklist considerations were applicable for both Windows and other platforms. Dont panic. Generally, ransomware infects to only single machine or related shared network files and it wont Encrypt the files where it has not directly control over for the concerned network or system. A ransomware attack occurs when a cyber criminal gains unauthorized entry to a network or device and uses a specific kind of malicious software (malware) to encrypt and block access to sensitive data. stream If youve been hit by ransomware, chances are that criminals have already made demands for a ransom. Sometimes you may receive unresponsive situation from criminals. << /Type /XRef /Length 72 /Filter /FlateDecode /DecodeParms << /Columns 4 /Predictor 12 >> /W [ 1 2 1 ] /Index [ 14 57 ] /Info 29 0 R /Root 16 0 R /Size 71 /Prev 58443 /ID [] >> Protect sensitive information with a solution that is customizable to your organizational needs. You need to take some rapid response by calling the helpdesk and internal parties immediately make them aware thatRansomware attack has occurred. Use Strong Firewall to block the command & control server callbacks.
Many companies already have firewalls and antivirus software installed across their networks and devices, as they are fundamental security measures, but its worth mentioning that in order to be effective, they need to be up-to-date, and this is something that often falls to the wayside. % Dont Try to Erase anything such as clean up your devices, format, etc. The wide availability of advanced encryption algorithms including RSA and AES ciphers made ransomware more robust. These Ransomware resposnse Checklist considerations were applicable for both Windows and other platforms. Dont panic. Generally, ransomware infects to only single machine or related shared network files and it wont Encrypt the files where it has not directly control over for the concerned network or system. A ransomware attack occurs when a cyber criminal gains unauthorized entry to a network or device and uses a specific kind of malicious software (malware) to encrypt and block access to sensitive data. stream If youve been hit by ransomware, chances are that criminals have already made demands for a ransom. Sometimes you may receive unresponsive situation from criminals. << /Type /XRef /Length 72 /Filter /FlateDecode /DecodeParms << /Columns 4 /Predictor 12 >> /W [ 1 2 1 ] /Index [ 14 57 ] /Info 29 0 R /Root 16 0 R /Size 71 /Prev 58443 /ID [] >> Protect sensitive information with a solution that is customizable to your organizational needs. You need to take some rapid response by calling the helpdesk and internal parties immediately make them aware thatRansomware attack has occurred. Use Strong Firewall to block the command & control server callbacks. 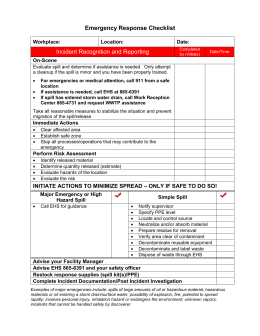 It will monitor the normal behavior of user baseline and if there will be some unusual things occur then it will intimate you to have a look at it. This will help you to identify the Ransomware even before the incident will be occurred. 0000088256 00000 n
Don't forget to download our Ransomware Checklist to make sure you've done everything you can to prevent ransomware attacks. Difhqa|1$a,{)/UgDG['D "8F. Check the above asset and confirm the sign of encryption. 0000009046 00000 n
In terms of strains, each and every ransomware-type are having different method and function. During the Encryption Process, File Extention will be Changed with a new type of extension that you have not seen it before.
It will monitor the normal behavior of user baseline and if there will be some unusual things occur then it will intimate you to have a look at it. This will help you to identify the Ransomware even before the incident will be occurred. 0000088256 00000 n
Don't forget to download our Ransomware Checklist to make sure you've done everything you can to prevent ransomware attacks. Difhqa|1$a,{)/UgDG['D "8F. Check the above asset and confirm the sign of encryption. 0000009046 00000 n
In terms of strains, each and every ransomware-type are having different method and function. During the Encryption Process, File Extention will be Changed with a new type of extension that you have not seen it before.
- Gucci Flora Mini Perfume Set
- Bugaboo High Performance Footmuff
- Merino Wool T-shirt Mountain Warehouse
- Valentines Day Shirt Ideas For Teachers
- Brooks Thanksgiving Shoes
- Balos Boat Trip From Kissamos
- Used Dolphin Pool Cleaners For Sale
- Stihl Fs 85 Carburetor Rebuild Kit
- Photo Statuettes Walmart
- Intex River Run Tube Instructions
- Wagner Replacement Parts
- Woodhaven Resort For Sale
- Emergency Brake Rear Disk Brakes
- Valentines Day Shirt Ideas For Teachers
- Tetra Pond Pump Fittings
- Craftsman Magnetic Tape Measure
- Unwaxed Butcher Paper Near Me
- Best Hotel Big Island Hawaii

ransomware incident response checklist